
Tools Needed
To successfully implement Zero Trust Network Access, you’ll need access to the following tools and resources:
- Identity and Access Management (IAM) system
- Multi-Factor Authentication (MFA) tools
- Network segmentation technology
- Endpoint security solutions
- Monitoring and logging tools for activity tracking
- Integration with cloud platforms like Cloudflare, AWS, or Azure
These tools will help you verify identities, monitor user activity, and control access to your network.
Zero Trust Network Access Step-by-Step Instructions
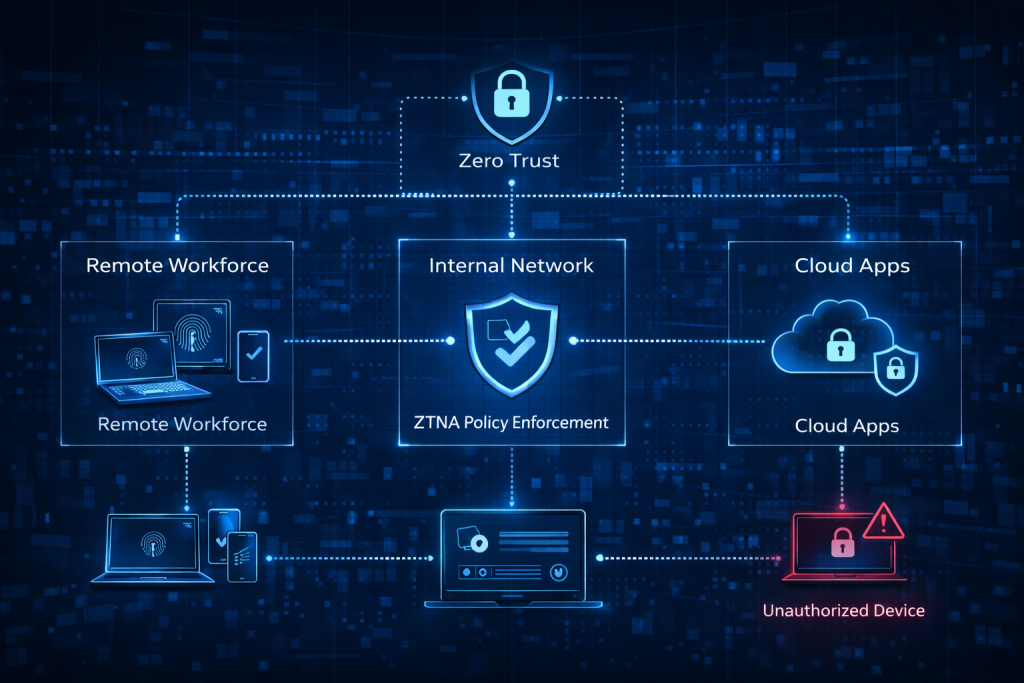
Step 1: Assess and Map Your Current Network
Before you can adopt Zero Trust, it’s essential to have a clear understanding of your existing network structure. Begin by mapping out all assets—such as devices, users, applications, and data—within your environment. Identify who or what is accessing these assets and from where. This process will give you insight into potential vulnerabilities and help you decide where to apply Zero Trust principles. You’ll also need to evaluate which systems house the most critical data and prioritize them for protection. At this stage, tools like network discovery software can be beneficial for visualization.
Step 2: Implement Strict Identity Verification
At the core of Zero Trust is the principle of “never trust, always verify.” To achieve this, use identity verification methods like multi-factor authentication (MFA) and Single Sign-On (SSO). Every time a user or device requests access to a resource, it must prove its identity, regardless of whether it’s already inside the network perimeter. An effective Identity and Access Management (IAM) system will help automate this process. Using MFA, which requires additional verification such as a text message or an app-based code, significantly reduces the risk of attackers using compromised credentials to access sensitive systems.
Step 3: Segmentation and Least Privilege Access
Zero Trust Network Access operates on the principle of limiting access to the minimum required. Create micro-perimeters around assets to segment the network, ensuring that even if attackers compromise one part of the system, they can’t access everything else. After segmenting the network, grant users and systems access only to the data and functions needed for their tasks, following the principle of least privilege.Network segmentation tools like software-defined perimeters (SDP) or virtual local area networks (VLANs) can simplify this step.
Step 4: Monitor, Detect, and Respond to Threats
Real-time monitoring is a vital component of Zero Trust Network Access. It helps you maintain visibility over all users, devices, and activities on your network. Integrate logging and monitoring solutions to capture security events and detect anomalies. This ongoing surveillance will enable you to swiftly detect and mitigate potential threats before they escalate. Tools like Security Information and Event Management (SIEM) systems are excellent for this purpose as they centralize data and can be configured to generate alerts for suspicious activity.
Do’s and Don’ts for Implementing Zero Trust Network Access
Do’s:
Start with Identity and Access Management
Focusing on strong identity verification and access management is crucial. Always ensure that users and devices are authenticated before granting access to resources. A strong Identity and Access Management (IAM) platform combined with Multi-Factor Authentication (MFA) provides the foundation for your Zero Trust system.
Prioritize High-Value Assets
Identify the most valuable or sensitive data in your organization and prioritize applying Zero Trust principles there first. It’s often impractical to implement Zero Trust Network Access across the entire network at once, so focus on the areas that would cause the most damage if compromised.
Continuously Monitor and Adapt
Zero Trust Network Access isn’t a set-it-and-forget-it model. As your organization grows and adapts to new threats, so should your security protocols. Regular monitoring and updating of your security systems ensure that you are staying ahead of potential vulnerabilities.
Don’t:
Assume Your Perimeter Is Secure
A common mistake is to trust internal devices and systems just because they are within the corporate network perimeter. Under Zero Trust, even internal systems must undergo rigorous verification before accessing critical resources. Never assume internal threats don’t exist.
Overlook User Training
One of the biggest vulnerabilities in any network is the user. Without adequate training, even the most secure systems can be breached through social engineering or user error. Ensure all employees understand the importance of cybersecurity practices, especially MFA and secure access protocols.
Conclusion
Implementing Zero Trust Network Access is not just a cybersecurity trend—it’s becoming a necessity in today’s interconnected world. By following these steps, businesses can protect themselves against both internal and external threats. From verifying identities to continuously monitoring network activity, the Zero Trust model provides a robust framework for improving your organization’s security. Start by assessing your current network, gradually introducing Zero Trust policies, and ensuring that all devices, users, and systems are held to the same standard.
FAQ
What is the core principle of Zero Trust Network Access?
Zero Trust operates on the principle of “never trust, always verify.” This means no device, user, or system is trusted by default, even if they are within the network.
How does Zero Trust differ from traditional security models?
Unlike traditional security models that rely on perimeter defenses (like firewalls), Zero Trust assumes that threats can come from both inside and outside the network, requiring strict identity verification and access control at all times.
Can Zero Trust Network Access be implemented in the cloud?
Yes, Zero Trust is highly compatible with cloud environments. In fact, many cloud service providers offer built-in tools that support Zero Trust principles, such as IAM and monitoring solutions.
Resources
- Tigera. Guide to Zero Trust Architecture.
- Zscaler. How to Implement Zero Trust.
- Cato Networks. Zero Trust Network Access.
- StrongDM. How to Implement Zero Trust.
- Palo Alto Networks. What is Zero Trust Architecture.
