In today’s ever-evolving digital landscape, threats lurk in every corner. As businesses grow increasingly reliant on online systems, the need to safeguard sensitive data becomes critical. Within the cybersecurity space, one name often stands out, Qualys. This cloud-based security and compliance solution empowers users to gain real-time visibility into their IT assets, identify vulnerabilities, and ensure regulatory compliance without the typical operational headaches of traditional systems.
Why does this matter to you? Because if you’re an IT manager, security analyst, or system administrator, integrating a tool like it can significantly reduce your exposure to risk. It helps you understand your network better, see where weaknesses lie, and fix them quickly before hackers can exploit them. The following guide walks you through the setup, usage, and optimization, offering tips from hands-on experience and highlighting potential pitfalls along the way.
Materials or Tools Needed
Before diving into configuration or scanning, you’ll need a few essentials to get started. Having the right tools and access permissions ensures a smoother setup and optimal use of the platform.
| Material or Tool | Purpose |
|---|---|
| Active Subscription | Grants platform access including VM, WAS, and PC modules |
| Administrative Privileges | Required for scan authentication and patch applications |
| Target Devices or IP Ranges | Defines scope of your vulnerability scans |
| Modern Web Browser | Interface access through Chrome, Firefox, or Edge |
| Compliance Documentation | Helps match scan results to auditing and regulatory needs |
This checklist ensures that you can hit the ground running without unnecessary delays during the setup process.
Qualys Instructions
Step 1: Set Up Your Qualys Account

Your journey begins with a subscription. Once your organization sets up the license, you’ll receive credentials to log into the dashboard. Visit the portal and enter your login information. As you enter the console, you’ll be prompted to select your modules, Vulnerability Management, Web Application Scanning, or Policy Compliance, depending on your cybersecurity objectives.
Initial setup includes configuring user roles and access permissions. Security team members may require different levels of access than network admins. By customizing these permissions early, you avoid bottlenecks later.
Step 2: Define and Map Assets
Asset definition is a foundational step. Qualys allows you to map assets through IPs, hostnames, or even dynamic tags. Navigate to the Asset Management module, where you’ll categorize devices based on organizational structure, geography, or security tier. Creating logical groups makes scan management easier later on.
Think of this step as building a directory of everything you own digitally — without knowing what’s in your environment, you can’t protect it. Ensure that cloud services, endpoints, servers, and network equipment are all accounted for.
Step 3: Schedule Vulnerability Scans
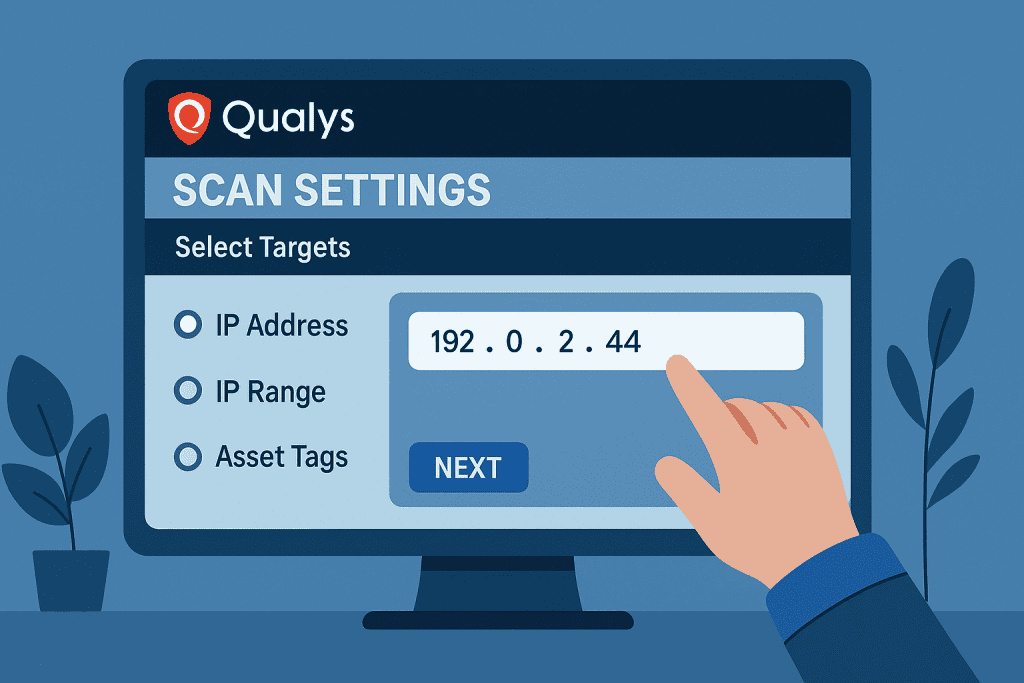
Go to the Vulnerability Management section and choose “Scans.” Click on “New Scan” and then define your target group. You can run authenticated or unauthenticated scans. Authenticated scans offer deeper insights, as they access system configurations and installed software.
For efficiency, schedule scans during off-peak hours. Doing this prevents network slowdowns and minimizes disruption. If your environment changes frequently, consider running scans daily. Otherwise, weekly scans are a safe baseline.
Step 4: Review Scan Results
Once your scans complete, access the Reports section. Each vulnerability listed includes a CVE identifier, severity rating, and mitigation steps. The dashboard visualizes this data using heatmaps and charts, allowing teams to prioritize effectively.
Reviewing scan results regularly ensures that nothing critical slips through the cracks. It also helps teams align with ongoing compliance standards such as PCI-DSS or HIPAA. Custom filters can further segment vulnerabilities by severity or asset group.
Step 5: Patch and Remediate
After identifying the risks, it’s time for action. Qualys offers guidance on how to fix each issue. In some cases, the remediation involves a simple patch. In others, configuration changes or updates to access controls may be necessary.
If you’re using a patch management system, integrate it to streamline the process. You can also track remediation efforts directly in the dashboard, which helps during audits. Always document fixes — especially those related to high or critical severity vulnerabilities — to maintain an audit trail.
Tips and Warnings
The power of Qualys lies not only in scanning but in how you use its features day to day. Below are tested tips and common pitfalls to avoid.
Tips for Better Results
| Tip | Why It Matters |
|---|---|
| Start with a test scan | Helps uncover misconfigurations or firewall issues early |
| Tag assets for clarity | Makes reporting and scanning easier to manage |
| Customize user roles | Limits access to sensitive scan and patch data |
| Export reports for stakeholders | Converts technical data into decision-friendly formats |
Common Mistakes to Avoid
| Mistake | Consequence |
|---|---|
| Running full scans on live systems | May degrade performance or disrupt users |
| Ignoring warning-level vulnerabilities | These can still be exploited — don’t overlook them |
| Skipping post-patch verification | Leaves room for incomplete fixes or rollback vulnerabilities |
Another useful tip: periodically audit your asset groups. New devices get added often and without clear tagging or categorization, they might not get scanned. This can leave hidden gaps that attackers might exploit.
Conclusion
The cybersecurity field waits for no one. Organizations need to act proactively rather than reactively, and tools like Qualys help make that possible. By following the setup steps, mapping your assets accurately, scheduling consistent scans, reviewing results critically, and patching with urgency, you create a stronger security posture.
Remember, cybersecurity is not a one-time task. It’s an ongoing strategy that adapts with threats. With this guide in hand, you’re not just using it, you’re mastering it.
FAQs
What is Qualys used for in cybersecurity?
Qualys is a cloud-based platform that identifies and helps fix vulnerabilities in digital environments. It aids cybersecurity professionals in reducing exposure and staying compliant with regulations.
How does Qualys improve vulnerability management?
Qualys enhances vulnerability management by automating scans, providing detailed reports, and recommending mitigation actions. This ensures continuous monitoring and fast response to potential threats.
Is Qualys effective for remote asset scanning?
Yes, Qualys works well for both on-premise and cloud-based assets. It uses external and internal sensors to perform thorough scans, making it highly effective for dispersed infrastructures.
Resources
- DevOps School. What is Qualys and Use Cases
- Escape Tech. Qualys DAST 2 Overview
- Security Studio. Qualys Scanning Guide
- Medium. Ultimate Guide to Qualys Vulnerability Management
- Securus360. VA Scanner Preparation Guide
