In today’s digital world, mastering Perimeter 81 within the cybersecurity space is not just a smart move, it’s a necessity. As cyber threats become more advanced, businesses must upgrade how they protect sensitive data and manage remote connections. Perimeter 81 provides a flexible and comprehensive solution that helps organizations secure their networks, simplify remote access, and maintain full control over who accesses their systems.
Whether you are an IT professional, a small business owner, or just someone curious about modern cybersecurity, understanding how it works can transform the way you think about digital safety. By the end of this guide, you will see why it’s a go-to tool for organizations looking to strengthen their cyber defenses and stay ahead of potential risks.
Perimeter 81 Materials or Tools Needed
Before you start configuring, it’s important to gather all the necessary tools and resources. Here’s a quick overview:
| Material / Tool | Purpose |
|---|---|
| Perimeter 81 subscription | Core software for cybersecurity management |
| Admin credentials | Access to configure your network |
| Compatible devices | Ensure endpoints are ready for connection |
| VPN client (optional) | Enhances secure remote access |
Having these essentials on hand will make the setup smoother and help you avoid common roadblocks.
Perimeter 81 Instructions
Step 1: Set Up Your Account
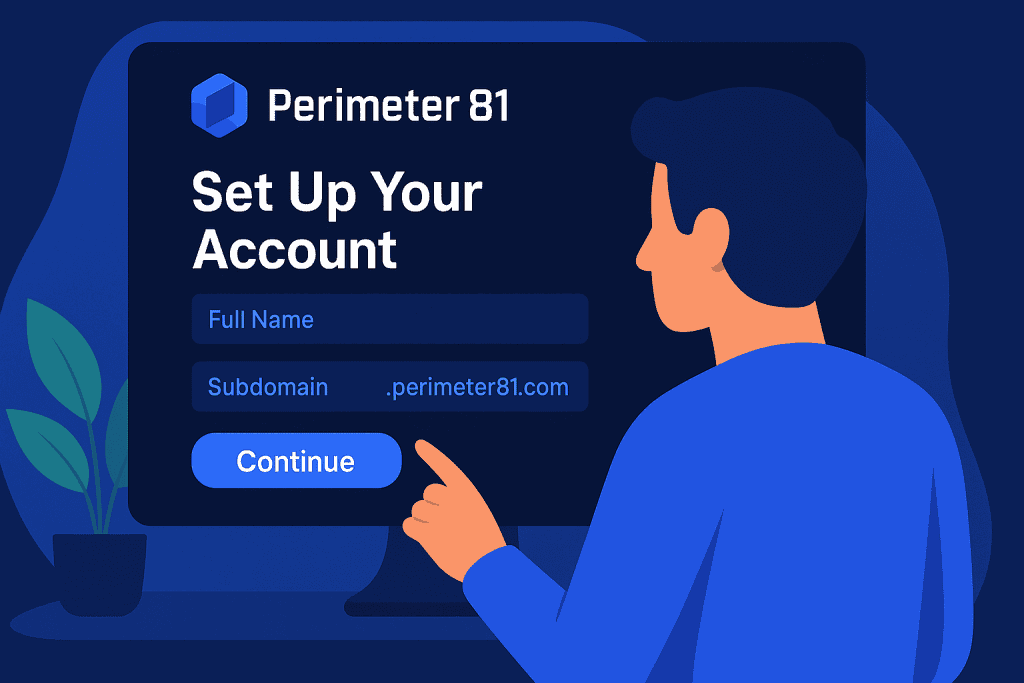
Start by creating your account. Use your admin credentials to log in and create your organization’s workspace. Here, you will enter company details, set up user groups, and assign roles to each team member. It’s a straightforward process, but don’t rush through it. A well-configured account lays the groundwork for secure and effective network management. Think of it as setting the foundation for a strong cybersecurity wall, one that keeps unauthorized users at bay.
Step 2: Configure Network Settings
Once your account is ready, it’s time to configure the network. The dashboard allows you to create secure gateways, assign IP addresses, and integrate essential cloud services. Pay close attention to firewall settings, making sure they align with company policies. Also, ensure compatibility with tools like Windows Update, so you maintain security without disrupting routine operations. This stage is critical because it shapes how your entire system interacts with external services and protects against breaches.
Step 3: Install Perimeter 81 Clients
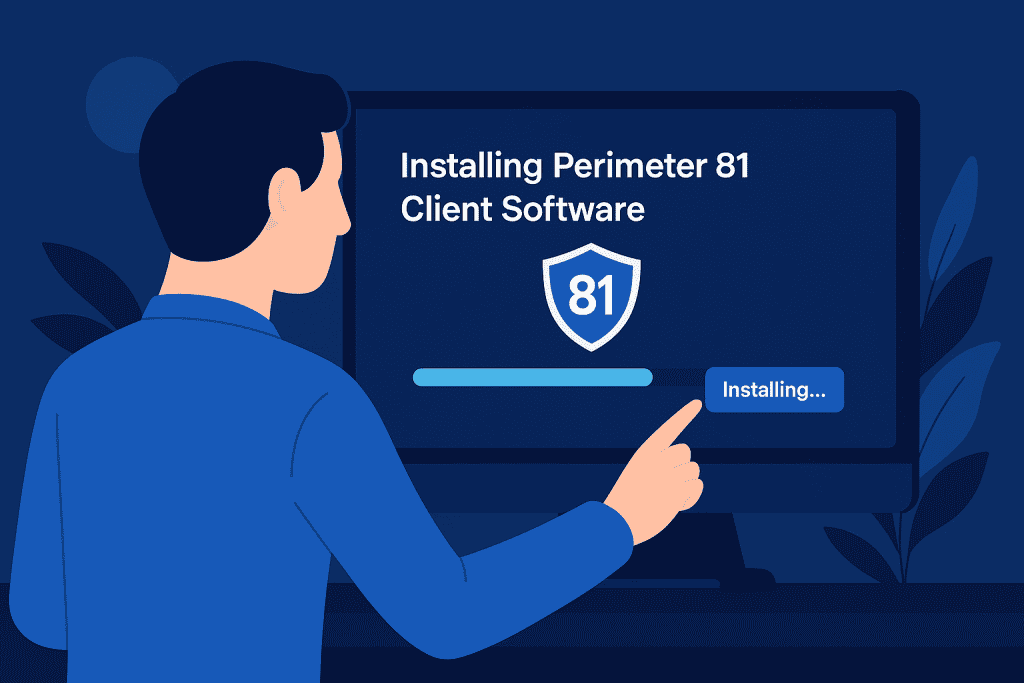
With the network configuration complete, move on to installing clients on all devices. This includes desktops, laptops, and mobile devices. Each endpoint must authenticate through it’s secure system. Provide your team with clear instructions on how to install the client and connect to the network. After installation, conduct connectivity tests to ensure that everything syncs smoothly. This step not only enhances security but also improves the user experience for your employees.
Step 4: Implement Security Policies
Now that devices are connected, it’s time to set your security policies. Define access permissions, set up multi-factor authentication, and, if needed, integrate with tools like Express VPN for an added layer of protection. Customizing these policies ensures that each user has the right level of access without exposing sensitive areas of your network. This is where you take full control of your cybersecurity environment, shaping it to match the needs of your organization while reducing vulnerabilities.
Step 5: Monitor and Optimize
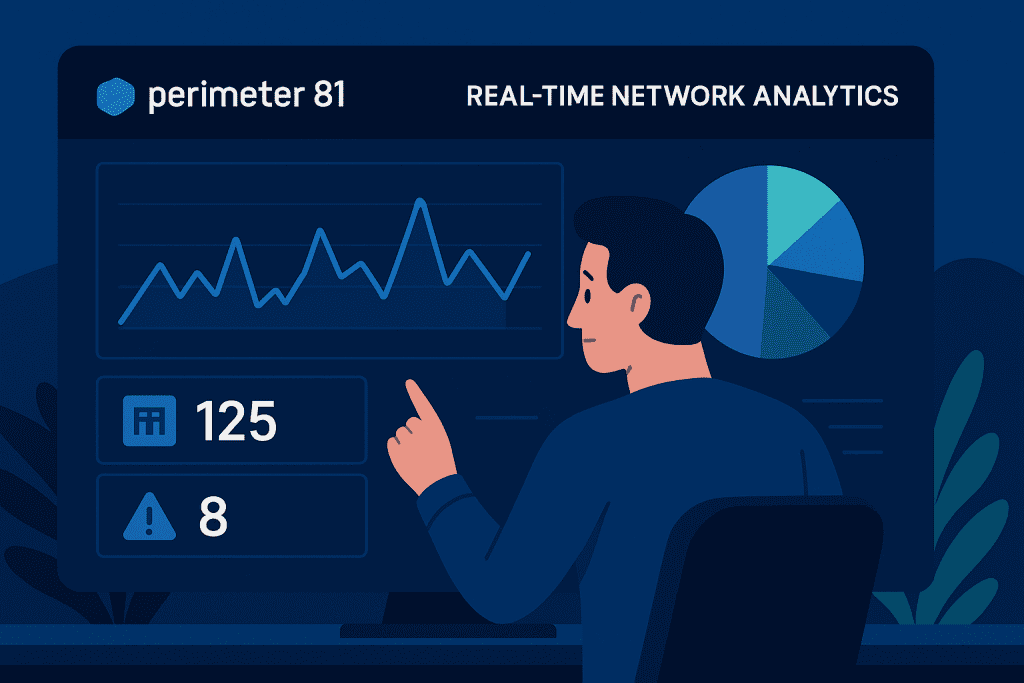
After everything is set up, regular monitoring becomes the key to success. Use it’s real-time analytics to track network traffic, identify potential threats, and optimize performance. Keep an eye out for unusual patterns that might signal hacking attempts or malware infiltration. Regularly updating your configurations and conducting audits will help keep your network resilient. Remember, cybersecurity is not a one-time fix, it’s an ongoing process that requires continuous attention and improvement.
Perimeter 81 Tips and Warnings
Implementing Perimeter 81 effectively takes more than just following the steps, it requires a thoughtful approach and ongoing diligence.
| Tips | Warnings |
|---|---|
| Keep all software and clients updated | Avoid using default passwords |
| Educate staff on safe digital behavior | Back up configurations before changes |
| Test changes in a sandbox before rollout | Overly strict rules can disrupt workflows |
It’s also important to stay aware of emerging threats, such as deepfakes, that can slip past traditional security measures. By combining advanced tools with smart practices, you give your organization the best chance to stay protected.
Conclusion
Deploying and managing Perimeter 81 gives businesses a dynamic advantage in today’s challenging cybersecurity environment. With its cloud-based approach, flexible configurations, and real-time analytics, you can transform your security strategy from reactive to proactive. Following these steps not only strengthens your defenses but also boosts overall efficiency and user confidence. Don’t leave your systems vulnerable, take charge with and build a safer, more reliable digital future.
Remember that cybersecurity is not a one-time project, it’s an ongoing commitment. Regularly review your network policies, stay informed about emerging threats, and use Perimeter 81’s analytics tools to make data-driven improvements. By making cybersecurity a priority today, you set the stage for long-term success and peace of mind tomorrow. So why wait? Start your journey toward a stronger, safer digital environment and empower your business to thrive in a secure, connected world.
FAQs
How does Perimeter 81 enhance cybersecurity for remote workers?
Perimeter 81 provides secure, encrypted access through cloud-based gateways, ensuring that remote employees connect safely without exposing sensitive company data to cyber threats.
What sets Perimeter 81 apart from traditional VPNs in cybersecurity?
Unlike traditional VPNs, Perimeter 81 offers a modern, cloud-native approach with zero-trust architecture, making it easier to manage, scale, and integrate with other security tools.
Can Perimeter 81 help detect advanced threats like deepfakes?
While Perimeter 81 focuses on network security, its real-time monitoring and analytics can help flag suspicious activity patterns, offering early warnings that support defense against emerging threats, including deepfake-driven attacks.
Resources
- BleepingComputer. Perimeter 81 Review
- Coralogix. Perimeter 81 Integration
- PeerSpot. Perimeter 81 Feedback
- PLI Support. Troubleshooting Perimeter 81
- TechRepublic. Perimeter 81 Review
