how to
-
How to Invest in S&P 500: A Beginner’s Guide
Starting your investing journey can feel like standing at the edge of a pool, unsure of whether to jump in. But just like swimming, once…
-
Sui Crypto Price: How to Track and Analyze Market Movements
Understanding the Sui Crypto Price in today’s fast-paced cryptocurrency market isn’t just for seasoned investors—it’s for anyone who wants to make smarter financial decisions. Whether…
-
Elevenlabs: How to Create Realistic AI Voices
The rise of artificial intelligence in voice synthesis has taken a significant leap with ElevenLabs, a powerful and user-friendly tool that’s redefining what we know…
-
Veracode Ultimate Guide: Mastering Secure Integration Fast
If you’re a developer navigating the ever-evolving world of cybersecurity, then you’ve likely heard about Veracode—a leading name in appsec tools. Whether you’re a security-conscious…
-

Polkadot Staking How-To: Earn Rewards with DOT
Alt text: Investor staking DOT tokens on a crypto wallet interface. Welcome to the world of Polkadot staking. This method lets you earn rewards by…
-

BlackRock Bitcoin ETF: Step-by-Step Investment Tutorial
The buzz around cryptocurrency never stops. And right now, the spotlight is on the Blackrock Bitcoin ETF. If you’re into digital assets or curious about…
-
How to Implement Varonis: A Step-by-Step Data-Centric Security Guide
Cybersecurity professionals know that protecting sensitive information is essential to maintaining trust and staying compliant with modern data regulations. For companies seeking to monitor file…
-
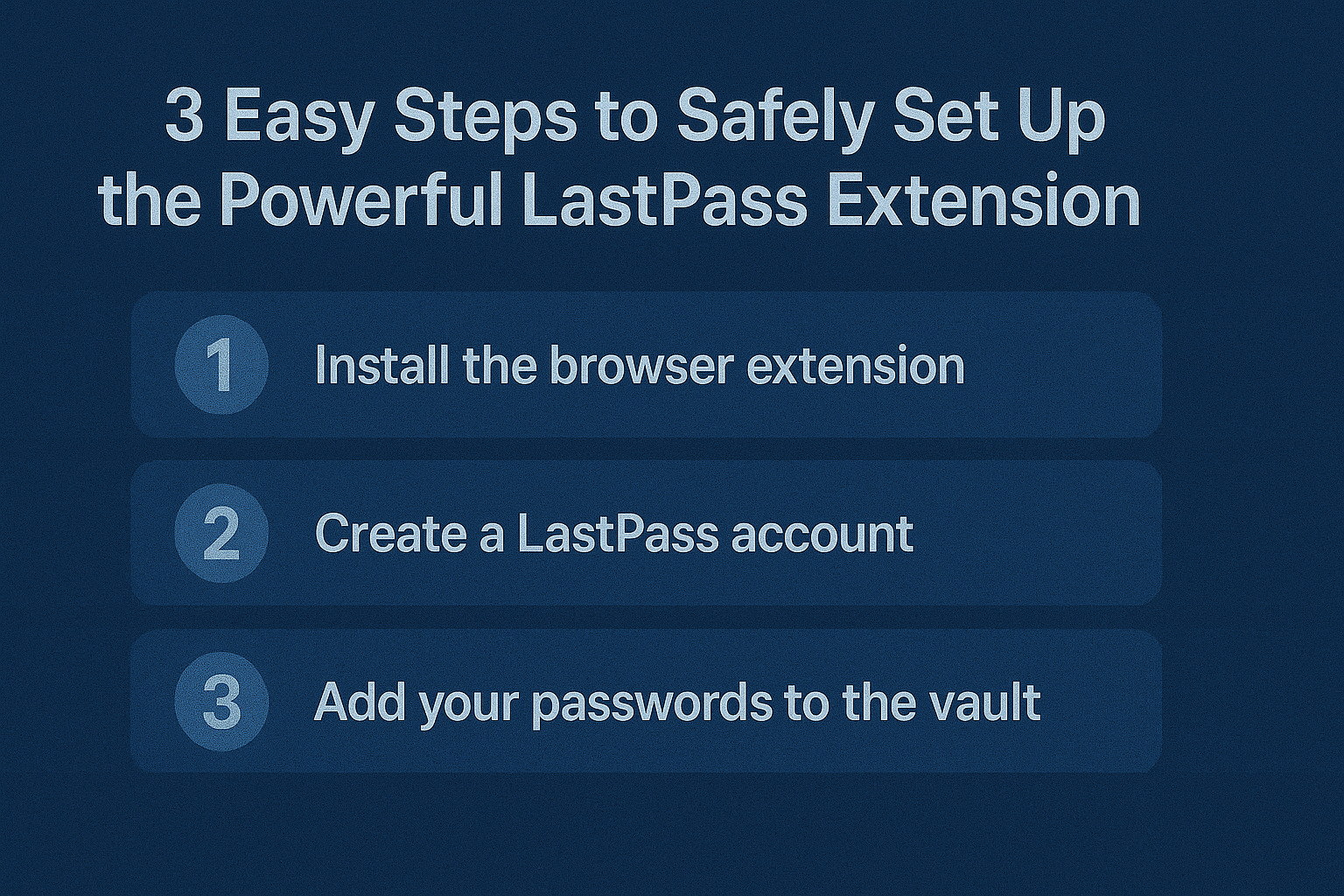
LastPass Extension: Turbocharge Password Safety in 3 Steps
In today’s digital jungle, where login screens pop up like mushrooms after rain, the LastPass Extension emerges as a life-saving tool for anyone who’s tired…
-
Master the Art of a Security Audit in 7 Simple Steps
If your company’s data were a fortress, then a security audit would be your routine castle inspection. Over time, cracks form in walls, doors loosen,…
-
Crypto30x.com: 7 Powerful Ways to Navigate Like a Pro
Navigating the world of cryptocurrency can feel like stepping into a dense jungle—thrilling yet unpredictable. That’s why having a powerful and intuitive platform like Crypto30x.com…
