how to
-
How to Get Started with Yield Farming
Yield farming has become one of the hottest trends in cryptocurrency, particularly in the decentralized finance (DeFi) space. This method of earning passive income through…
-

How to Set Up a Security Operations Center: A Step-by-Step Guide
In today’s rapidly evolving digital world, setting up a Security Operations Center (SOC) has become crucial for businesses aiming to protect their data and maintain…
-

Powerful Revit Tasks Automation with Dynamo
The first time I automated a repetitive workflow, I felt like I’d finally stopped wrestling my model and started directing it. If you’ve ever spent…
-

How to Generate Income with Covered Calls: Step-by-Step Guide
Covered calls are a strategic options trading method often used by investors to generate additional income from their stock holdings. This approach is especially beneficial…
-

How to Recover from a Crypto Ransomware Attack?
Crypto ransomware has become a significant threat in the world of cryptocurrency, with cybercriminals locking away sensitive data and demanding large sums in crypto payments.…
-

How to Mitigate Zero-Day Vulnerabilities in Cybersecurity?
Zero-day vulnerabilities are a critical issue in cybersecurity, representing weaknesses in software that are exploited before the vendor can develop and release a patch. For…
-

How to Create a Dynamic Block in AutoCAD: Step-by-Step Guide
The first time I built a dynamic block in AutoCAD, it felt like I’d unlocked a cheat code—suddenly one door block could become every door…
-
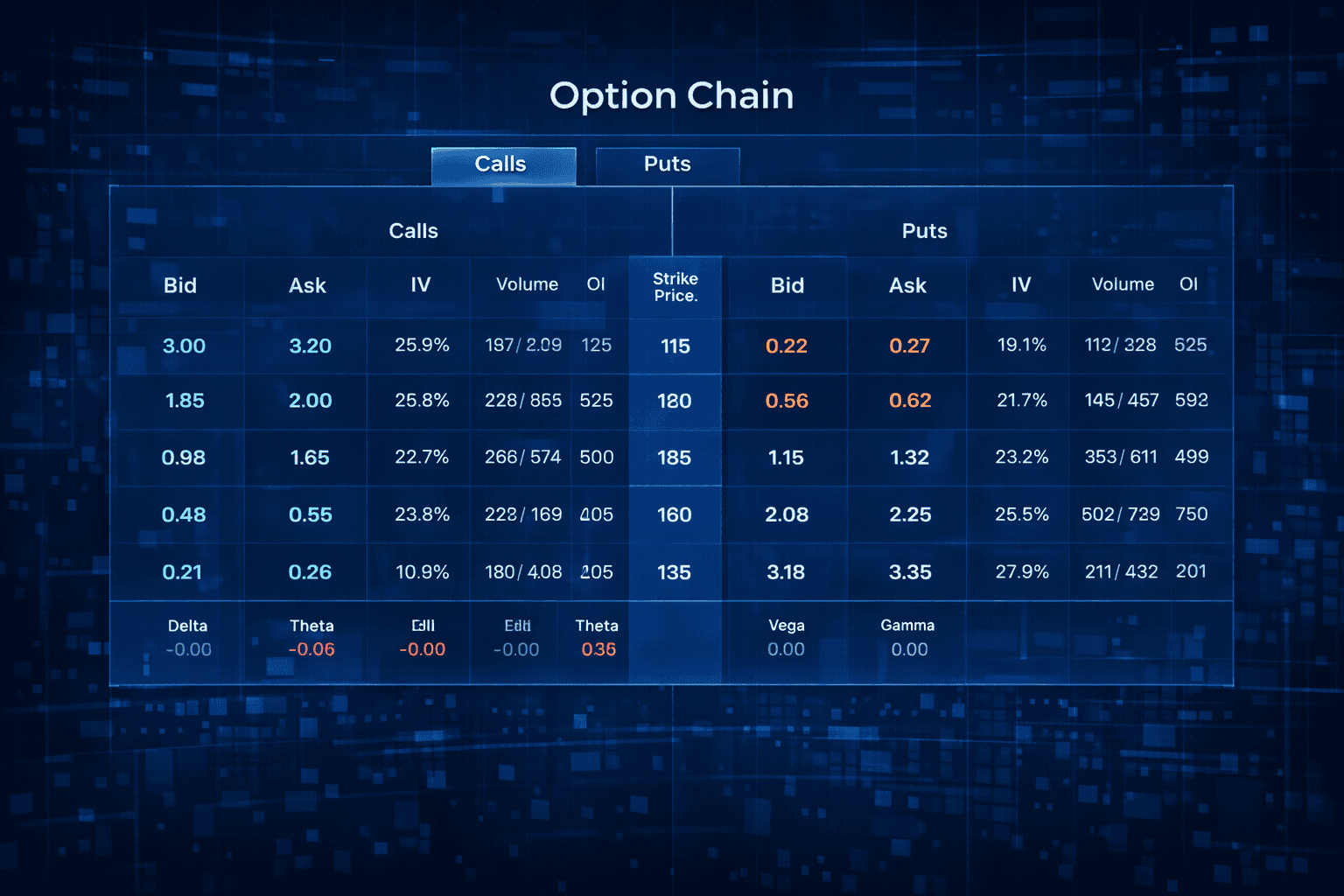
Option Chain: 4 Powerful Steps for Smart Trading
In today’s fast-paced financial markets, understanding how to read an option chain is essential for investors, especially those working with popular stocks like Tesla (TSLA),…
-

Fight Night: 4 Exciting Steps to Buy Today
Buying a new token can feel a lot like walking into a packed arena before the first bell rings. There is noise, excitement, opinions flying…
-

DeFi Protocol: 4 Powerful Steps for Success
The combination of NFTs (Non-Fungible Tokens) and DeFi (Decentralized Finance) is transforming the cryptocurrency world. This integration opens up new horizons for artists, investors, and…
