Cyber threats are evolving faster than ever, making cybersecurity a top priority for businesses and individuals alike. If you’ve ever felt overwhelmed by the complexities of protecting your digital assets, you’re not alone. Fortunately, the NIST Cybersecurity Framework (NIST CSF) is here to help.
Originally designed for government agencies, this framework has become the gold standard for organizations of all sizes, helping them identify, protect, detect, respond to, and recover from cyber threats.
But let’s be honest—reading about cybersecurity frameworks can be dry. So, let’s make this fun! Whether you’re a tech pro or a small business owner just trying to keep hackers at bay, this guide will break down how to implement the NIST Cybersecurity Framework in a way that’s practical, straightforward, and even a little enjoyable.
Materials or Tools Needed
Before diving into implementation, let’s make sure you have everything you need.
| Tool/Requirement | Purpose |
|---|---|
| NIST Cybersecurity Framework (CSF) Document | Official reference for implementation. |
| Risk Assessment Tools | Helps identify potential security threats. |
| Security Policies & Procedures | Existing cybersecurity protocols in your organization. |
| Access to IT Infrastructure | Needed for audits and security checks. |
| Security Team or Consultant | Optional but helpful for expert guidance. |
If you’re handling cybersecurity for a large organization, you may also need specialized security software, compliance checklists, and monitoring tools to track vulnerabilities.
Step-by-Step Instructions
1. Understand Your Current Cybersecurity Posture
Before implementing the NIST Cybersecurity Framework, you need to assess where you currently stand. Think of this as a security check-up for your organization.
- Conduct a risk assessment to identify vulnerabilities.
- Review your current security policies and procedures.
- Examine past security breaches (if any) to understand your weaknesses.
- Identify your most critical assets—data, networks, and IoT devices.
Once you have a clear picture of your cybersecurity status, it’s time to move forward.
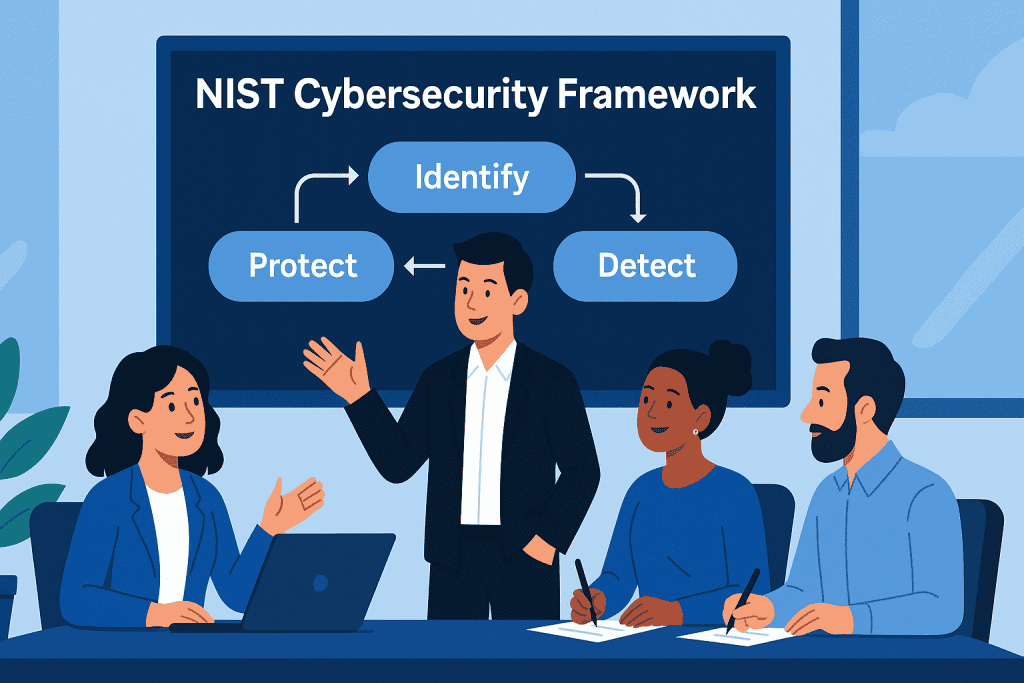
2. Map Your Security Strategy to the NIST Framework
The NIST CSF is built around five core functions:
- Identify – Understand your assets, risks, and business environment.
- Protect – Develop safeguards to minimize security risks.
- Detect – Implement monitoring tools to catch threats in real time.
- Respond – Have a plan in place to handle security incidents.
- Recover – Establish recovery plans to restore normal operations after an attack.
For each of these areas, align your existing security policies or create new ones to meet NIST CSF guidelines.
3. Implement Security Controls and Safeguards
Now it’s time to put your security measures into action!
- Set up firewalls and encryption to protect sensitive data.
- Implement multi-factor authentication (MFA) to secure user access.
- Use advanced technology like AI-driven threat detection.
- Ensure all software is up to date to prevent vulnerabilities.
- Develop cybersecurity training programs for employees.
Security isn’t just about technology—it’s also about human behavior. Train your staff to recognize phishing emails and suspicious activity.
4. Monitor, Detect, and Respond to Threats
Cyber threats are constantly evolving, so continuous monitoring is essential.
- Install automated threat detection systems to identify attacks in real time.
- Conduct regular security audits to spot weaknesses before hackers do.
- Develop an incident response plan outlining what to do if a breach occurs.
- Maintain cybersecurity logs to track suspicious activity.
The best security system in the world is useless if no one is watching. Proactive monitoring helps prevent small issues from turning into full-scale cyber disasters.
5. Keep Evolving with the Framework
The NIST Cybersecurity Framework isn’t a one-and-done deal—it’s a continuous process. Cyber threats change, and your security measures should too.
- Regularly update your cybersecurity policies based on new risks.
- Adopt futuristic technology to stay ahead of hackers.
- Follow industry trends and innovation in cybersecurity.
New inventions are emerging every day, and hackers are always looking for new ways to exploit vulnerabilities. Stay ahead of the curve by continuously improving your cybersecurity strategy.
Tips and Warnings
| Tip | Explanation |
|---|---|
| Start Small | If you’re new to NIST CSF, focus on one function at a time. |
| Use Automation | AI-powered security tools can detect threats faster than humans. |
| Involve Everyone | Cybersecurity is a company-wide effort, not just an IT problem. |
| Review Regularly | Set a schedule to revisit and refine your security strategies. |
Common Mistakes to Avoid

- Ignoring Employee Training – Most cyber breaches happen due to human error, yet many organizations fail to train employees on phishing, password security, and safe online practices.
- Focusing Only on Technology, Not Strategy – Relying solely on security software without clear policies, risk assessments, or response plans leaves gaps in cybersecurity defenses.
- Not Testing Incident Response Plans – Having a security plan is useless if it’s never tested; unprepared teams often struggle to respond effectively during a real cyberattack.
- Underestimating IoT Devices as Security Risks – Smart devices often have weak security settings, making them easy entry points for hackers to infiltrate networks.
- Failing to Update and Patch Systems – Outdated software and unpatched vulnerabilities are common attack vectors, yet many organizations delay crucial updates.
- Lack of Continuous Monitoring – Cyber threats evolve daily, but some organizations fail to monitor their networks, allowing security breaches to go undetected.
By avoiding these mistakes, organizations can strengthen their cybersecurity defenses and ensure they are fully aligned with the NIST Cybersecurity Framework.
Conclusion
The NIST Cybersecurity Framework isn’t just a set of guidelines—it’s a powerful roadmap that can help protect your business from cyber threats. By understanding your current security posture, implementing safeguards, and continuously evolving your strategy, you can build a robust cybersecurity defense.
Whether you’re a small business owner or managing enterprise-level security, staying ahead of threats is key. Now, it’s your turn to implement these steps and take control of your cybersecurity future!
FAQ
What is the NIST Cybersecurity Framework, and why is it important?
The NIST Cybersecurity Framework is a set of best practices designed to help organizations improve their cybersecurity posture. It’s important because it provides a structured approach to identifying, preventing, detecting, responding to, and recovering from cyber threats.
How does the NIST Cybersecurity Framework apply to small businesses?
Small businesses are prime targets for cyberattacks due to limited security resources. The NIST CSF helps small businesses prioritize their security efforts, implement cost-effective protections, and reduce their risk of cyber threats.
How can IoT devices be secured using the NIST Cybersecurity Framework?
IoT devices are often vulnerable to cyberattacks. To secure them: Change default passwords. Update firmware regularly. Use network segmentation to separate IoT devices from critical systems. Follow NIST CSF guidelines to enhance overall security.
Resources
- ION247. Implementing the NIST Cybersecurity Framework: A Guide for Financial Institutions.
- ZenGRC. The Complete Guide to the NIST Cybersecurity Framework.
- IBM. Understanding the NIST Cybersecurity Framework.
- YouTube. NIST Cybersecurity Framework Implementation Guide.
- X. Incident Response Guidelines Based on NIST Framework.
