In today’s fast-paced digital world, keeping your data safe is like guarding a treasure chest in a storm. Within the cybersecurity realm, Fortinet stands as a titan, offering trusted, cutting-edge solutions. Cybersecurity isn’t just for tech giants—it’s essential for businesses and everyday users alike. Fortinet cybersecurity solutions provide the right tools to strengthen your defenses, enhance operational security, and provide peace of mind for fans and professionals striving to stay ahead of cyber threats. Whether you run a small business, a global enterprise, or simply want to protect your home network, it has something valuable to offer.
With cyber threats constantly evolving, you cannot afford to take risks. Choosing the right cybersecurity tools makes all the difference between thriving securely or falling victim to attacks. That’s why understanding and implementing Fortinet cybersecurity solutions is a must. Let’s dive into the essentials that will get you started on the right track.
Materials or Tools Needed
Before diving into the world of Fortinet cybersecurity solutions, you need a few essentials to make the most out of the experience. Proper preparation ensures a smoother setup and effective results.
| Materials/Tools | Purpose |
|---|---|
| Fortinet FortiGate | Firewall security appliance to guard network |
| FortiAnalyzer | Data analytics and security reporting tool |
| FortiManager | Device management and configuration center |
| Fortinet Security Fabric | Integrated system for real-time response |
| Reliable Internet Connection | Ensures continuous, updated protection |
Using these tools, you can manage, monitor, and secure your network seamlessly. Don’t overlook the importance of having a good internet connection—it acts as the lifeline connecting all your Fortinet products to perform optimally.
Fortinet Instructions
Step 1: Setting Up Your Account

Starting your journey with Fortinet cybersecurity solutions begins with creating an account. Go to it’s official site and click “Sign Up.” Here, you will provide basic information such as your name, organization, and role. Once registered, you gain access to the its Customer Support Portal, product downloads, licenses, and security advisories.
An active account ensures you receive critical updates and support. Remember to verify your email address to unlock all functionalities and premium features.
Step 2: Installing FortiGate Firewall
The FortiGate Firewall is the heart of Fortinet cybersecurity solutions. Download the firmware or unbox your FortiGate appliance. Installation is straightforward—connect the appliance to your internet gateway, power it up, and access the setup wizard via your web browser.
Follow the wizard carefully: assign a secure admin password, configure internal and external interfaces, and activate key security services. Testing your setup with a basic internet browsing check will confirm that your firewall is functioning as intended.
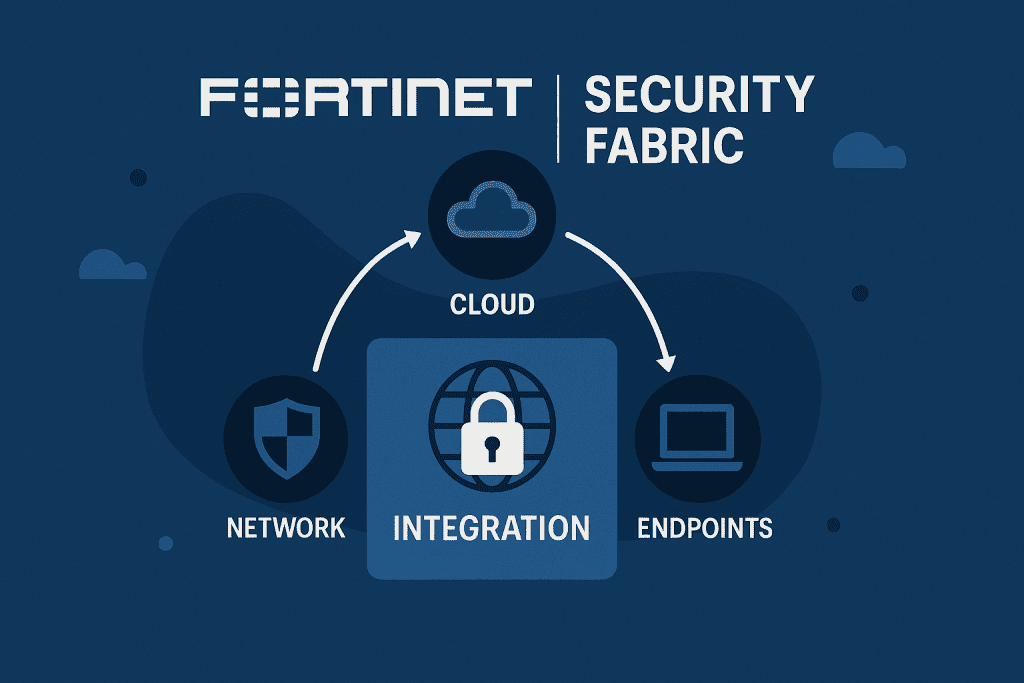
Step 3: Integrating Fortinet Security Fabric
To take full advantage of Fortinet cybersecurity solutions, integrate the Fortinet Security Fabric. This feature connects your FortiGate Firewall, FortiAnalyzer, and FortiManager into one powerful security network.
Begin by accessing your FortiGate dashboard and enabling Fabric Connectors. You can link endpoints, cloud security services, sandbox analysis, and threat intelligence feeds. This real-time sharing ensures threats are identified and neutralized swiftly, offering maximum protection without manual interventions.
Step 4: Activating FortiAnalyzer
FortiAnalyzer offers deep security analytics, enabling you to make smarter decisions. Install it by downloading the FortiAnalyzer image or using a physical device. After installation, connect it to your FortiGate by configuring Log Forwarding.
Once connected, you’ll start receiving real-time logs and alerts. This tool provides valuable insights into traffic anomalies, potential breaches, and system health, allowing proactive risk mitigation.
Step 5: Configuring FortiManager
Managing its multiple devices becomes a breeze with FortiManager. Deploy it either as a cloud service or hardware appliance. Connect your FortiGate devices to FortiManager and configure it to push centralized policy updates.
With FortiManager, you can apply security patches, automate backup schedules, and manage device health reports. It ensures your cybersecurity infrastructure remains updated and consistent across all touchpoints.
Tips and Warnings
When working with this cybersecurity solutions, staying sharp can make all the difference. Here’s a combined table of important tips to maximize success—and the common mistakes you must avoid.
| Tips for Success | Mistakes to Avoid | How to Overcome |
|---|---|---|
| Update Regularly: Always apply firmware and security patches. | Ignoring firmware updates | Set up automated update notifications through FortiManager. |
| Enable FortiGuard Services: Subscribe to real-time threat intelligence. | Misconfigured security rules | Test all new firewall policies in a controlled environment before pushing live. |
| Use Role-Based Access: Assign the least privilege needed to admin accounts. | Neglecting endpoint protection | Deploy FortiClient to extend protection to all endpoints. |
| Monitor Logs Frequently: Analyze logs through FortiAnalyzer to detect issues early. | Delayed threat response | Set up automatic alerts for critical events and unusual activities. |
| Train Your Staff: Regular training reduces human error. | Human errors causing breaches | Implement cybersecurity awareness programs and phishing simulations. |
Staying proactive is the name of the game. Cyber threats evolve rapidly, but a properly managed Fortinet cybersecurity solution puts you two steps ahead.
Conclusion
Building a strong defense with this cybersecurity solutions is easier than you might think. By following the steps detailed above—setting up your account, installing FortiGate, integrating the Security Fabric, and utilizing FortiAnalyzer and FortiManager—you set yourself up for success.
Cybersecurity is not a one-time effort but an ongoing journey. With this at your side, your network, devices, and data remain shielded against even the most sophisticated threats. Take the first step today, strengthen your digital fortress, and enjoy greater peace of mind in our increasingly connected world.
FAQs
How does Fortinet help businesses in cybersecurity?
It provide businesses with integrated security through firewalls, cloud security, threat analytics, and endpoint protection, ensuring full coverage against modern cyber threats.
Can Fortinet cybersecurity solutions be used at home?
Yes, Fortinet solutions like FortiGate can secure home networks, offering enterprise-level protection against hackers, phishing attempts, and malware even for personal setups.
What makes Fortinet better compared to other cybersecurity providers?
Fortinet stands out with its Security Fabric architecture, centralized management tools, real-time threat intelligence from FortiGuard, and scalability, making it ideal for both small businesses and large enterprises.
Resources
- Fortinet. Getting Started with FortiGate 7.6.0
- Twitter. Fortinet’s Latest Innovations
- YouTube. FortiGate Overview Video
- FortiGuard Labs. Real-Time Threat Intelligence
- Yahoo Finance. Fortinet (FTNT) Stock Performance Overview
