What Is Spyware? If you’ve ever wondered how personal data suddenly leaks, how ads seem to follow you around, or how passwords vanish from accounts, spyware could be the hidden culprit. In cybersecurity, spyware represents one of the most deceptive dangers because it operates silently while stealing valuable information.
Understanding what is spyware is vital for anyone using the internet. Attackers rely on its stealth to monitor, manipulate, or exploit users without detection. From personal devices to corporate networks, spyware compromises privacy and security. In today’s world of cyber threats, deepfakes, and advanced hacking techniques, knowing how spyware works is a shield against digital manipulation.
What Is Spyware?
What Is Spyware is malicious software designed to secretly monitor user activity and gather sensitive data. It tracks keystrokes, browsing habits, and even login credentials. Often, users don’t realize it’s running because spyware hides deep inside the system.
Synonyms include “malware surveillance,” “tracking software,” and “digital snooping tools.” In simple terms, spyware is like an invisible spy sitting in your computer or phone, watching your every move.
Breaking Down Spyware
To understand what is spyware, imagine leaving your house keys with a stranger who follows you everywhere. They don’t break in loudly. Instead, they watch silently, record your routines, and know when to strike. That’s how spyware functions in the digital world.
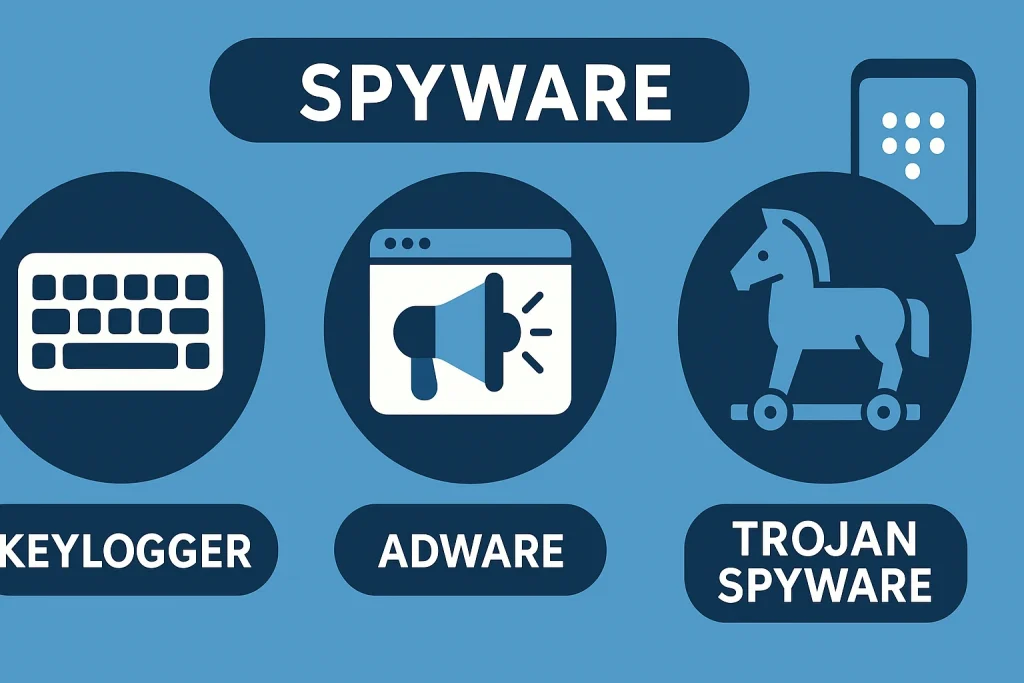
Spyware has several components:
- Keyloggers: These record every keystroke, capturing passwords, messages, and bank details.
- Adware: Spyware that floods your device with intrusive ads while collecting browsing habits.
- Trojan-based spyware: Malware disguised as legitimate software to trick you into installing it.
- System monitors: Programs that track activity across emails, chats, and apps.
Take keyloggers as an example. You might type your Bitcoin wallet credentials thinking it’s safe, but spyware records every keystroke. Meanwhile, adware might track shopping habits, then bombard you with targeted ads. Though less dangerous than financial theft, this invasion of privacy shows why spyware is harmful.
Unlike obvious malware, spyware often arrives bundled with legitimate downloads or fake Windows Update prompts. Once installed, it operates quietly, making detection difficult. For corporations, this can mean massive data leaks. For individuals, it might mean stolen identities, drained bank accounts, or exposure to scams in the crypto market or coin market.
The worst part? Spyware doesn’t need flashy tricks. It thrives on deception, proving that in cybersecurity, silence can be deadlier than noise.
History of Spyware
What Is Spyware dates back to the early days of the internet when tracking tools evolved from harmless cookies into malicious programs.
| Year | Event |
|---|---|
| 1990s | Rise of adware and early spyware |
| 2000s | Growth of keyloggers and Trojan spyware |
| 2010s | Advanced spyware used in corporate espionage |
| 2020s | AI-powered spyware and surveillance with deepfakes |
Types of Spyware

Spyware comes in many forms, each targeting users differently.
Keyloggers
Keyloggers capture every keystroke typed. This makes them dangerous for stealing banking details, emails, and passwords.
Adware
Adware tracks browsing behavior to display tailored ads. While some adware seems harmless, it often collects excessive personal data.
System Monitors
These tools oversee everything from emails to chats, giving attackers full visibility of your activities.
Trojan Spyware
Hidden inside seemingly safe software, Trojan spyware fools users into downloading it. Once active, it compromises entire systems.
| Type | Description |
|---|---|
| Keyloggers | Record keystrokes to steal sensitive info |
| Adware | Tracks browsing and delivers ads |
| System Monitors | Track full device activity |
| Trojan Spyware | Disguised as legitimate software |
How Does Spyware Work?
Spyware infiltrates devices through downloads, malicious links, or fake pop-ups. Once installed, it hides in the background. It collects data—like browsing patterns, login credentials, or private chats—and sends it back to attackers. This process often goes unnoticed, making it especially dangerous compared to other malware.
Pros & Cons
From an attacker’s perspective, spyware has strengths and weaknesses.
| Pros | Cons |
|---|---|
| Stealthy and hard to detect | Security software can block it |
| Provides valuable data | Slows down devices |
| Works on individuals and corporations | Risk of exposure during scans |
Uses of Spyware
Understanding the uses of what is spyware is essential because it shows how attackers exploit different environments, from personal devices to entire industries. Spyware may seem like a single category of malware, but its applications are wide-ranging, and each use carries unique risks.
Personal Data Theft
One of the most common uses of what is spyware is stealing personal information. Cybercriminals harvest usernames, passwords, banking details, or even medical records. Imagine typing your credit card details into an online store. If spyware lurks on your device, that information is instantly captured. Victims often discover this too late, after money vanishes or their identity is used for fraud.
Corporate Espionage
In the corporate world, spyware is a tool for large-scale theft. Attackers use it to infiltrate company networks, steal intellectual property, and gain access to confidential strategies. Competitors might deploy spyware to learn about upcoming products or innovations, turning it into a weapon for business advantage. In some cases, spyware has cost companies millions by exposing client records, trade secrets, and sensitive financial data.
Government Surveillance
Another controversial use of what is spyware comes from government agencies. Some governments deploy advanced spyware to track citizens, journalists, or activists. While often justified as national security, this raises concerns about privacy and human rights. The rise of AI-driven spyware, combined with deepfakes, makes it even harder for people to tell whether their conversations or devices are being monitored.
Financial Manipulation
Spyware is also used in scams tied to the crypto market or online trading. Attackers track users exploring coin market platforms or blockchain wallets, waiting for the perfect moment to strike. Even a single stolen Bitcoin key can translate into massive financial loss. In other cases, spyware delivers fake ads promoting shady investment opportunities, convincing victims to put money into scams.
Everyday Inconvenience
Not all spyware use is headline-worthy. Sometimes it’s just about flooding devices with ads, slowing performance, or tracking browsing habits. While this may sound less severe, the invasion of privacy and exposure to unwanted content still compromise user trust. Even those relying on Express VPN for online privacy cannot escape spyware already embedded in the system.
The many uses of what is spyware highlight why it is such a persistent issue in cyber threats. It blends into ordinary digital life, stealing information silently while appearing harmless. From high-stakes espionage to everyday annoyance, spyware proves that no device, business, or government is immune.
Conclusion
Spyware is one of the most deceptive cyber threats because it hides in plain sight, quietly stealing data while victims remain unaware. From personal identity theft to corporate espionage and even government surveillance, its impact spans every level of digital life. The best defense lies in awareness, cautious online behavior, and strong security practices. In a world where silence can be deadlier than noise, recognizing and stopping spyware is essential to protecting both privacy and trust.
Resources
- Kaspersky – What is Spyware?
- Norton – Spyware Explained
- McAfee – Spyware and How to Remove It
- CISA – Understanding Spyware
- Trend Micro – What is Spyware?
