Picture this: a hacker sitting in front of multiple screens, typing furiously not to steal data, but to save it. This is the fascinating world of ethical hacking, a vital branch of cybersecurity that turns the art of hacking into a force for good.
In today’s digital jungle, threats lurk in every corner phishing scams, ransomware attacks, and identity thefts. Organizations are constantly under siege from invisible enemies. That’s where ethical hackers come in: they think like the bad guys to protect us from them.
What Is Ethical Hacking?
Ethical hacking, sometimes called “penetration testing” or “white-hat hacking,” is the practice of intentionally breaking into computer systems with permission to find vulnerabilities before malicious hackers do.
Unlike cybercriminals, ethical hackers operate within legal boundaries, often under a contract that outlines what they can and cannot test. Their findings help organizations patch weaknesses before real attackers exploit them.
Breaking Down Ethical Hacking
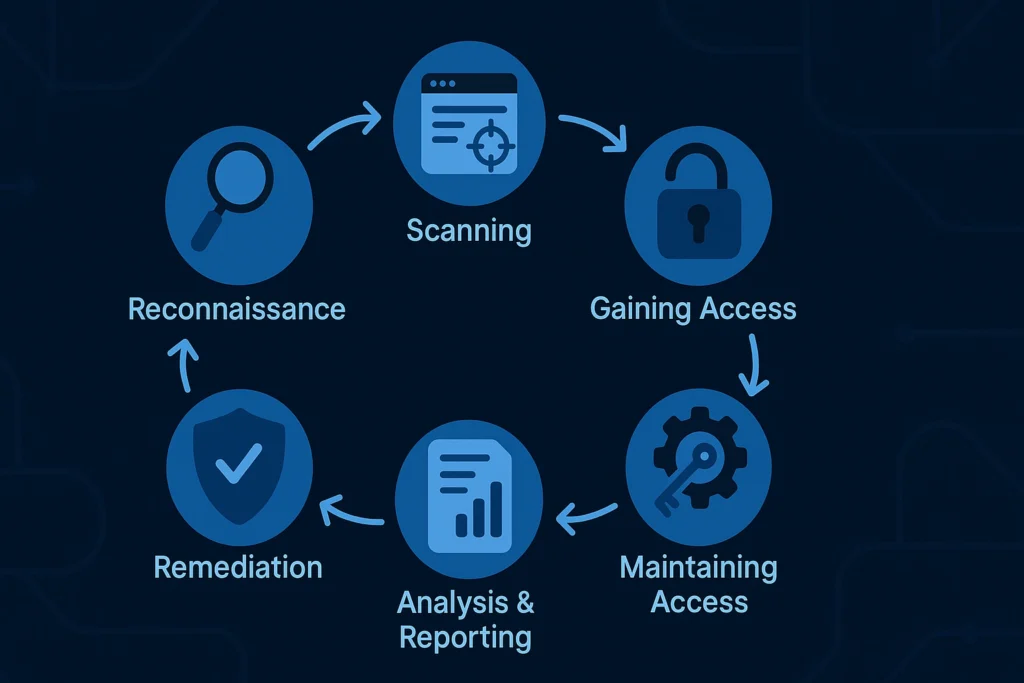
Reconnaissance
Before any digital lock-picking begins, the ethical hacker starts with reconnaissance the art of information gathering. Much like a detective observing a crime scene, they study the target system, collect publicly available data, and identify potential entry points. This step lays the groundwork for the entire ethical hacking process.
Scanning
Once the groundwork is set, it’s time to dig deeper. Scanning involves using specialized tools to detect open ports, outdated software, and other vulnerabilities within a network. Ethical hackers rely on scanners like Nmap or Nessus to uncover hidden weaknesses that could become potential gateways for intruders.
Gaining Access
Here’s where the real test begins. In this stage, ethical hackers simulate a genuine cyberattack to determine how easily they can breach the system. They may exploit discovered vulnerabilities to see how far they can go all within authorized limits. It’s a controlled experiment designed to expose flaws before real attackers can exploit them.
Maintaining Access
Sometimes, breaking in is only half the battle. Ethical hackers also assess how long they could stay within a system without detection. This phase tests persistence and the effectiveness of intrusion detection systems. The goal isn’t to cause harm, but to ensure that organizations can spot and stop unauthorized access quickly.
Analysis and Reporting
Finally comes the reflection stage analysis and reporting. Here, ethical hackers document every vulnerability, every test, and every finding in a detailed report. They translate technical results into clear recommendations that help businesses strengthen their defenses and prepare for future threats.
History of Ethical Hacking
The concept of ethical hacking dates back to the 1970s, when the term “hacker” didn’t carry a negative meaning. Back then, it referred to computer enthusiasts who loved exploring systems just for the thrill of discovery.
| Year | Event |
|---|---|
| 1960s–70s | Hackers at MIT developed early computer programs and coined the term “hacker” for problem solvers. |
| 1980s | Cybercrime rose, leading to a need for security testing. The U.S. government began formal penetration testing. |
| 1990s | “Ethical hacking” became a recognized term. Companies like IBM started hiring white-hat hackers. |
| 2000s–Present | Ethical hacking evolved into a global industry, with certifications like CEH (Certified Ethical Hacker) setting professional standards. |
Types of Ethical Hacking
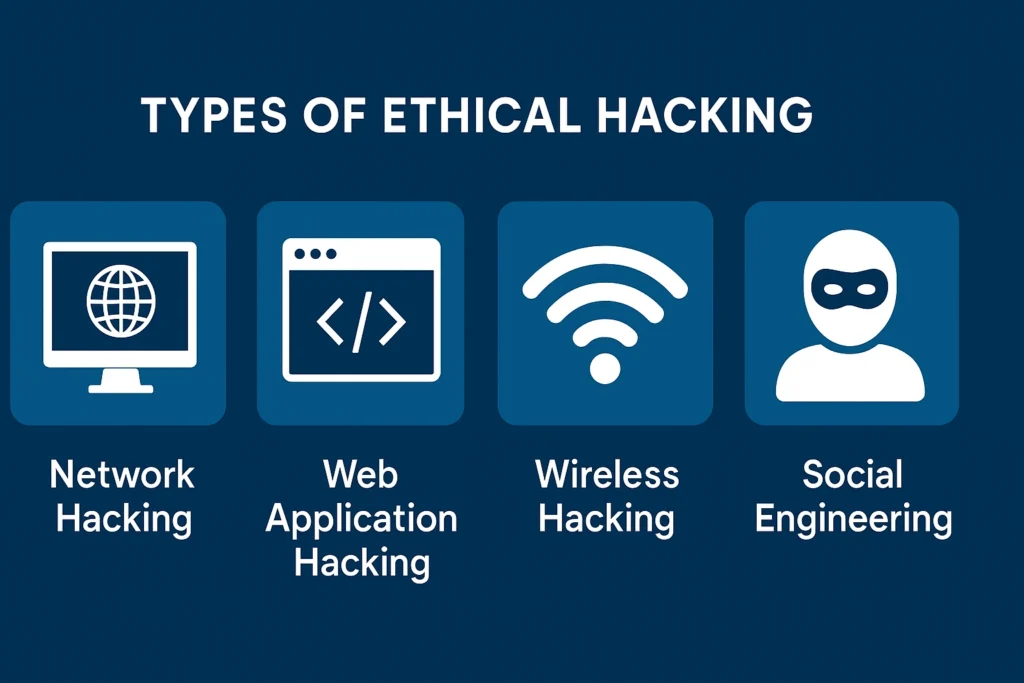
Ethical hacking isn’t one-size-fits-all. There are several types, each serving a specific purpose in protecting digital systems.
Web Application Hacking
Ethical hackers test websites and web apps for vulnerabilities like SQL injections or cross-site scripting (XSS). For instance, a hacker might test a banking app to ensure that customers’ data isn’t exposed through weak input validation.
Network Hacking
Here, hackers focus on routers, switches, and servers essentially the digital highways that connect us. They simulate attacks to check if firewalls and encryption are doing their job.
Wireless Network Hacking
Wi-Fi networks can be easy targets. Ethical hackers assess how secure wireless setups are, especially in public or enterprise environments where data flows freely.
Social Engineering
Not all hacking is technical. Sometimes, it’s psychological. Ethical hackers test human vulnerabilities by simulating phishing emails or fake login prompts to see if employees fall for them.
System Hacking
This type dives deep into operating systems. Ethical hackers exploit weaknesses to demonstrate how malware or unauthorized users might gain access and how to stop them.
How Does Ethical Hacking Work?
Think of ethical hacking as a scientific experiment. Every step has a purpose and follows a controlled sequence to uncover vulnerabilities responsibly. First, ethical hackers get authorization from the system owner. Then they plan the attack simulation, choosing tools like Nmap or Metasploit. After that, they execute tests, carefully recording every detail.
The results are analyzed to create a comprehensive vulnerability report, highlighting flaws and suggesting fixes. These reports often help organizations avoid massive losses. For instance, one famous case involved an ethical hacker who discovered a flaw in Facebook’s login process saving millions of users from potential credential theft.
Pros & Cons
Like any field, ethical hacking has both benefits and drawbacks. Let’s weigh them:
| Pros | Cons |
|---|---|
| Strengthens cybersecurity defenses | Can be costly for small businesses |
| Prevents data breaches | Risk of misuse if guidelines aren’t followed |
| Builds trust with clients and users | Requires constant learning and certification |
| Offers lucrative career paths | Legal and ethical lines must always be respected |
Uses of Ethical Hacking
The applications of ethical hacking are widespread, touching almost every sector that relies on digital systems.
Corporate Cybersecurity
Companies use ethical hacking to secure their networks, protect customer data, and comply with privacy regulations. For instance, financial institutions regularly hire ethical hackers to test online banking systems.
Government and Defense
National security agencies rely on ethical hackers to safeguard classified information and prevent cyber warfare. These professionals often work on highly sensitive missions.
Healthcare
Ethical hackers simulate potential ransomware or phishing attacks to identify vulnerabilities before cybercriminals can exploit them. Their proactive work helps safeguard not only private information but also the trust between patients and healthcare providers.
Education and Research
Academic institutions often handle valuable research data and intellectual property, making them attractive targets for cyberattacks. Ethical hackers help ensure that sensitive information such as research findings, academic records, and financial data remains secure.
E-commerce and Retail
In today’s competitive online marketplace, even one breach can destroy consumer trust. By conducting regular penetration tests, ethical hackers help retailers maintain smooth, secure transactions and protect brand reputation ensuring that both businesses and customers can shop with peace of mind.
Resources
- EC-Council: Certified Ethical Hacker (CEH)
- Kaspersky: Ethical Hacking Basics
- IBM: Security Learning Hub
- Cybrary: Ethical Hacking Course
- SANS Institute: Cybersecurity Training
