When discussing cybersecurity today, one term that constantly appears in headlines is data breach. But what is it, and why is it such a critical issue? In essence, it refers to unauthorized access, disclosure, or theft of sensitive information such as personal details, financial records, or corporate secrets. Reviewing the definition of breach incidents matters because they impact individuals, companies, and even governments worldwide. Beyond financial damage, breaches erode trust, stall innovation, and can even cause political instability when government systems are targeted. From leaked medical records affecting millions to corporate trade secrets being auctioned on dark web forums, the ripple effects are enormous.
In the digital age, cybercriminals exploit vulnerabilities through malware, phishing, or system flaws. Understanding the meaning of it is not just for IT experts—it’s vital for businesses protecting client trust and for everyday users safeguarding their identities. By knowing what a breach means and learning from past incidents, readers can adopt preventive strategies and recognize their role in building a safer digital future.

What is a Data Breach?
It is the exposure of confidential or protected data to unauthorized parties. This could involve hacking into a system, exploiting weak passwords, or accidental leaks by employees. The definition also includes cases where sensitive files are left unprotected on the internet.
From credit card numbers to medical records, the type of stolen information varies. What makes these events particularly alarming is their long-term effect: once personal details are compromised, they can circulate in black markets or be used for identity theft for years.
Breaking Down a Breach
Targeting
Hackers identify weak points in a network or database.
Intrusion
Unauthorized access is gained through malware, phishing, or insider threats.
Exfiltration
Data is copied, stolen, or leaked.
Exploitation
Information is sold, used for fraud, or leveraged for further attacks.
Each stage highlights vulnerabilities in digital infrastructure. Recognizing these stages allows organizations to implement strong detection and response systems.
History
The history of these incidents shows how attacks have evolved from simple hacks to advanced cybercrimes using ransomware and zero-day exploits. Below is a timeline of major milestones:
| Year | Milestone | Impact |
|---|---|---|
| Early 2000s | First large-scale corporate breaches | Millions of customer records stolen |
| 2013 | Yahoo breach | Over 3 billion accounts compromised |
| 2017 | Equifax hack | Exposed financial data of 147 million people |
| 2018–2020s | Marriott, Capital One, and others | Showed growing risk in cloud and global enterprises |
| Today | Ransomware and zero-day exploits | Breaches linked to global crime syndicates |
The history of these events teaches us how attacks evolve. Early intrusions relied on weak security practices, but today’s breaches often exploit sophisticated tools like ransomware or zero-day vulnerabilities. What are the lessons from history? Stronger password management, multi-factor authentication, and timely system updates are recurring themes.
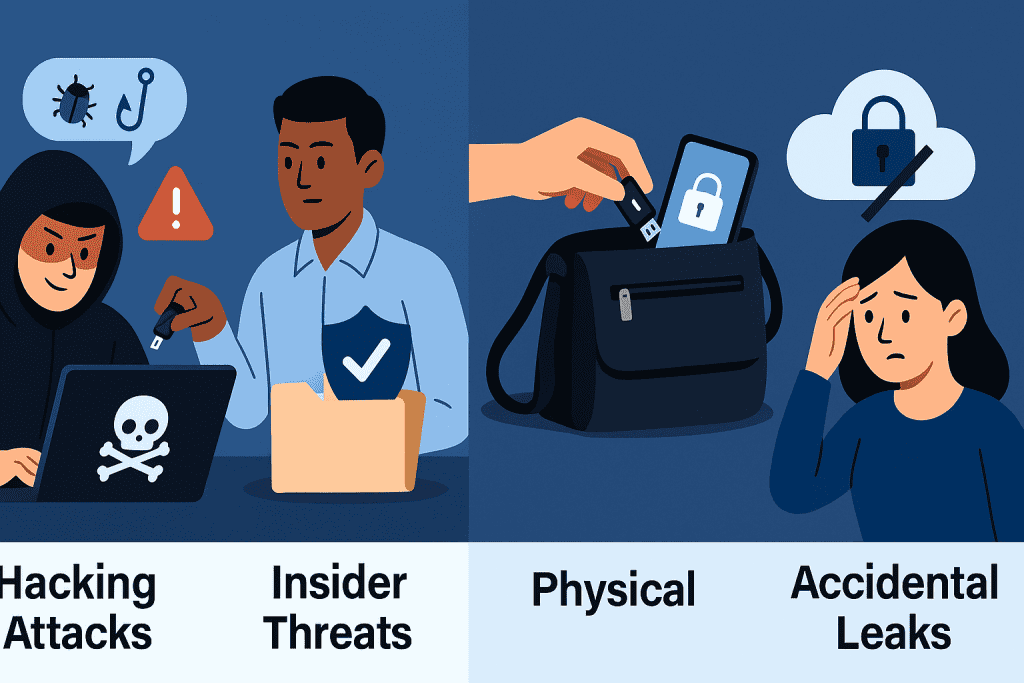
Types of Data Breach
Breaches come in different forms, and knowing them helps with building defenses.
| Type | Description | Example |
|---|---|---|
| Hacking Attacks | Criminals infiltrate databases using malware, phishing, or brute force | Stolen credentials from phishing emails |
| Insider Threats | Employees or contractors intentionally or accidentally expose data | Misuse of admin privileges |
| Physical | Lost or stolen devices with sensitive files | Missing company laptops |
| Accidental Leaks | Misconfigured cloud storage or weak access controls | Open AWS storage buckets |
Each type requires unique countermeasures, which is why no single tool can guarantee complete safety.
How Does a Breach Work?
It works like a chain reaction: once attackers find a loophole, they exploit it quickly. In many cases, the breach remains undetected for weeks or months. During this time, stolen information may already be circulating on underground forums. Criminals monetize data by selling credit card numbers, forging identities, or blackmailing companies into paying ransoms. What are the warning signs? Unusual login attempts, sudden spikes in network traffic, or unauthorized access alerts. By monitoring these signals, organizations can shorten the detection time and minimize damage. Businesses that implement advanced threat monitoring tools often reduce breach impact significantly.
What are the warning signs? Unusual login attempts, sudden spikes in network traffic, or unauthorized access alerts. By monitoring these signals, organizations can shorten the detection time and minimize damage.
Pros & Cons
While the events themselves are harmful, studying them has both advantages and drawbacks.
| Pros | Cons |
|---|---|
| Raises awareness among businesses and individuals | Constant headlines may create “breach fatigue” |
| Encourages stronger cybersecurity practices | Financial losses and reputational harm are severe for companies |
| Informs governments to create privacy regulations like GDPR | Victims may suffer long-term consequences such as identity theft |
Uses of Data Breach
Studying it isn’t just about learning from mistakes—it’s about applying insights to strengthen future defenses.
IBM. Cost of a Data Breach Report 2025
Provides businesses with in-depth analysis of financial, operational, and reputational impacts of breaches, helping leaders plan budgets, justify security investments, and strengthen compliance strategies.
NIST. Data Confidentiality: Detect, Respond to, and Recover from Data Breaches (SP 1800-29)
Offers practical guidance for detecting, responding to, and mitigating it, giving IT teams actionable frameworks to protect sensitive data across industries.
BigID Blog. The 8 Hidden Costs of a Data Breach (insights from IBM 2024 Report)
Highlights often overlooked consequences of it, such as regulatory fines, customer churn, and brand damage, expanding awareness beyond direct financial loss.
CSO Online. Security and privacy laws, regulations, and compliance: The complete guide
Explains how global regulations shape attack response, ensuring that businesses understand obligations under GDPR, HIPAA, and other compliance frameworks.
TechRadar. AI means data breaches now cost much less – but they’re still a huge threat to businesses
Analyzes the role of AI in detecting breaches faster, reducing average costs, while stressing that organizations must remain vigilant against evolving threats.
From businesses managing compliance audits to individuals creating stronger passwords, and governments shaping privacy laws, these resources demonstrate how its awareness powers better defenses across all levels of society.
Conclusion
It is more than a technical failure—it’s a global challenge that affects trust, security, and digital growth. The definition of it highlights unauthorized access, theft, or loss of sensitive data. While they cannot always be fully prevented, awareness and proactive strategies significantly reduce their impact. For readers, the key takeaway is clear: learn what it is, recognize the risks, and adopt practical steps to protect personal and organizational information.
Resources
- IBM. Cost of a Data Breach Report 2025
- NIST. Data Confidentiality: Detect, Respond to, and Recover from Data Breaches (SP 1800-29)
- BigID Blog. The 8 Hidden Costs of a Data Breach (insights from IBM 2024 Report)
- CSO Online. Security and privacy laws, regulations, and compliance: The complete guide
- TechRadar. AI means data breaches now cost much less – but they’re still a huge threat to businesses
