What is a Firewall? In the world of cybersecurity, this is one of the most important questions every internet user, business owner, and IT professional should understand. Think of it as a digital guard standing between your private network and the chaotic online space. It checks data traffic, allows safe connections, and blocks suspicious or harmful activity before it can cause damage.
I still remember the first time my computer was hit with malware. Without the protection of a it, my files and personal data could have been completely exposed. Whether you’re a casual user trying to keep personal photos secure or a company safeguarding customer information, this security measure plays a vital role. By the end of this guide, you’ll see how understanding and using one can help you stay safe in today’s connected world.
What is a Firewall?

It is a protective system designed to monitor and control both incoming and outgoing network traffic according to security rules. It serves as a barrier between a trusted internal network and the unpredictable outside internet. In simple terms, it decides which information is safe to pass through and which should be blocked.
Some people call it a “digital barrier” or “network shield.” Depending on the need, it can be a software program installed on your computer, a piece of hardware connected to your router, or even a combination of both. Its job is always the same: prevent harmful intrusions and maintain secure communication.
Breaking Down Firewall
Imagine your house with a locked front door. Only those you trust can enter, while strangers are kept out. That’s exactly how a firewall works in the digital world—it’s your first line of defense.
At the core of its operation are rules that determine which traffic gets through. These rules might block suspicious IP addresses, stop malicious software, or let trusted applications connect freely. For example, if an attacker attempts to sneak into your system, it examines the data, identifies the threat, and shuts it out before it can cause harm.
There are also different layers of protection. Some systems check packets of data as they move across networks, while others go deeper, analyzing applications and even user behavior. Advanced setups can detect unusual patterns that signal potential hacking attempts. A small business owner I know once faced an attack by bots trying to overload his website. His firewall quickly detected the unusual traffic surge and blocked it, saving his online store from going offline.
Firewalls evolve constantly to meet new challenges. Today, even cloud services, smart devices, and Windows Update downloads rely on them to ensure safe communication. Without this safeguard, connecting to the internet would be like leaving your house wide open without locks or cameras.
History of a Firewall
The idea is developed alongside the growth of the internet. What started as simple filters grew into complex systems that adapt to modern threats.
| Year | Development | Impact |
|---|---|---|
| 1980s | Packet-filtering firewalls | First line of basic defense |
| 1990s | Stateful inspection | Smarter tracking of sessions |
| 2000s | Next-generation firewalls | Application-level control |
| 2010s | Cloud-based firewalls | Secured virtual environments |
| Today | AI-driven firewalls | Detect complex patterns and advanced threats |
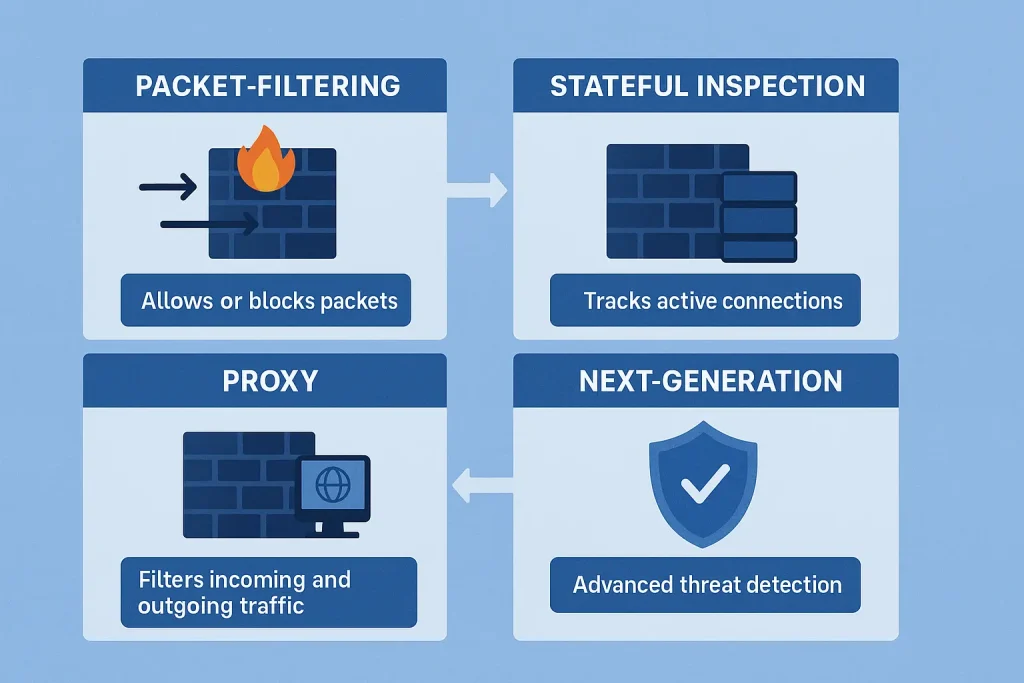
Types of Firewall
it come in different forms, each suited to specific needs.
Packet-Filtering Firewall
This is the simplest type, checking small chunks of data called packets against rules like IP addresses and ports.
Stateful Inspection Firewall
Goes a step further by monitoring the state of network connections, not just isolated packets.
Proxy Firewall
Acts as an intermediary, hiding the real network while analyzing traffic requests.
Next-Generation Firewall
Combines multiple advanced features like intrusion prevention, deep packet inspection, and application awareness.
| Type | Key Feature | Best For |
|---|---|---|
| Packet-Filtering | Basic traffic rules | Small setups |
| Stateful Inspection | Tracks active sessions | Businesses |
| Proxy Firewall | Hides internal network | High-security needs |
| Next-Generation | Advanced threat defense | Enterprises |
How does Firewall work?
The system works by applying security rules to every bit of traffic. Each packet of data is examined, compared to the rules, and then either allowed through or blocked. This process happens instantly, so harmful requests never reach your device. In modern environments, its often paired with antivirus programs and monitoring systems to form a layered defense.
Pros & Cons
Like any tool, it has benefits and drawbacks.
Pros
Stops unauthorized access
A firewall acts as a gatekeeper, preventing hackers, malicious software, and other unauthorized users from entering your network. This is especially important for protecting sensitive personal or business information.
Monitors suspicious data
It doesn’t just block entry—it also keeps an eye on the data traveling through your system. Suspicious patterns, like malware or phishing attempts, can be flagged before they cause real harm.
Provides alerts and logs
Firewalls record activity and create alerts when something unusual happens. These logs are valuable for diagnosing attacks, identifying weak points, and strengthening future defenses.
Essential for cybersecurity
In today’s digital world, no security system is complete without a firewall. It forms a core layer of protection against cyberattacks and is often required for regulatory compliance.
Cons
Can block safe traffic sometimes
Because firewalls are strict, they sometimes mistake safe websites, applications, or emails for threats. This can disrupt normal activities and frustrate users.
May reduce network speed
Since every piece of traffic has to be inspected, this extra layer of checking can slow down internet speeds or overall performance, especially if hardware is outdated.
Needs updates to stay effective
Cyber threats evolve rapidly. If a firewall is not updated regularly, it may fail to recognize and block newer forms of attacks, leaving the system vulnerable.
Can be complex to configure
Properly setting up a firewall requires technical knowledge. If it’s configured incorrectly, it can either block too much (causing issues) or too little (leaving gaps in security).
| Pros | Cons |
|---|---|
| Stops unauthorized access | Can block safe traffic sometimes |
| Monitors suspicious data | May reduce network speed |
| Provides alerts and logs | Needs updates to stay effective |
| Essential for cybersecurity | Can be complex to configure |
Uses of Firewalls
Its a versatile and used in many areas, from homes to large corporations.
Business Protection
Organizations use them to keep unauthorized users away from sensitive customer or employee data.
Personal Security
Home users rely on them to avoid malicious downloads, unsafe sites, and viruses.
Cloud Applications
As more services move to the cloud, it also adapt to safeguard virtual networks and cloud-hosted data.
Compliance and Regulations
Industries like healthcare and finance depend on them to meet strict security standards.
Think of them as the digital equivalent of Express VPN. Both act as shields—one hides your location and secures browsing, while the other guards your network itself. Without one, devices could be vulnerable to malware like Deepfakes, or exposed to relentless cyber threats that compromise privacy and trust.
Conclusion
Firewalls are more than just technical add-ons—they are the backbone of digital security, acting as vigilant gatekeepers that control traffic, block intrusions, and ensure safe connections, without which private data and networks would face constant threats. By understanding their types, history, and uses, you can better protect yourself and your organization, whether you’re browsing at home, running a small business, or managing enterprise systems. Configured wisely and kept updated, a firewall serves as the first and most reliable defense, securing your digital world with confidence.
Resources
- Fortinet : What Is A Firewall?
- Cisco : What Is A firewall?
- PaloAlto : IPS. vs. IDS vs. Firewall: What Are the Differences?
- Enterprise Networking Planet : 18 Types of Network Security Solutions to Implement
- Best Reviews: What Are IDS and IPS and How They Complement a VPN
