Trezor Wallet is more than just a gadget—it’s a lifeline for anyone serious about crypto security. In the world of crypto, where transactions are irreversible and digital theft is rampant, protecting your private keys is essential. Unlike online wallets that are vulnerable to constant attacks, this wallet keeps your assets safe offline.
When I bought my first Bitcoin, I remember being anxious about leaving it in an exchange. Stories of hacks and lost funds made me restless. The day I set up my Trezor Wallet, I felt a new level of confidence. It gave me control, freedom, and peace of mind. For crypto traders, long-term holders, or even beginners, understanding these wallet is the first step to safeguarding financial freedom.
What is Trezor Wallet?
It is a hardware device designed to store cryptocurrencies securely offline. Unlike software wallets connected to the internet, it is a physical piece of hardware that guards private keys against theft. Some users call it a “cold wallet” or “hardware wallet.” The main idea is to separate your private keys from the online environment, making it nearly impossible for attackers to steal them remotely.
Breaking Down Trezor Wallet
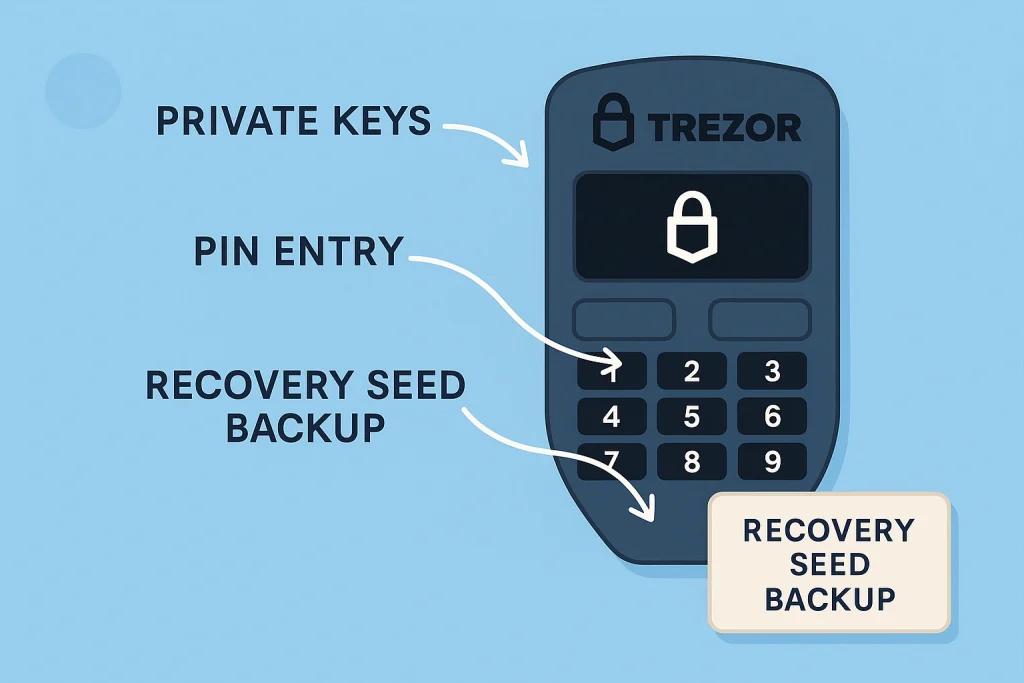
To break it down, Trezor Wallet works like a vault in your pocket. Your crypto private keys never leave the device, and transactions require physical confirmation. This reduces the risk of remote hacking or phishing attacks.
The wallet consists of:
- Hardware device: A small USB-like gadget with a screen and buttons.
- PIN and passphrase protection: Even if stolen, it cannot be accessed without your codes.
- Recovery seed: A unique set of words used to restore your wallet if the device is lost or damaged.
- Integration with apps: It connects to software like Trezor Suite to view balances and send transactions securely.
For example, if you want to send Bitcoin, you connect the device, enter your PIN, and confirm the transaction directly on the screen. The private keys never leave the wallet, which means even if your computer is infected with malware like Deoptakes, your crypto remains safe.
I once helped a friend recover his wallet after he accidentally damaged his device. With his recovery seed, he was able to restore everything in a brand-new wallet. That’s the power of planning with hardware security.
History of Trezor Wallet
The concept of hardware wallets emerged as cryptocurrencies gained popularity and online thefts increased. Trezor became the first widely adopted hardware wallet.
| Year | Event | Impact |
|---|---|---|
| 2013 | Founded by SatoshiLabs | First hardware wallet concept |
| 2014 | Launch of Trezor One | Made cold storage accessible |
| 2018 | Trezor Model T released | Added color screen & advanced features |
| 2020 | Integration with DeFi apps | Expanded usability |
| Today | Ongoing updates and upgrades | Continues as a top hardware wallet |
Types of Trezor Wallet

There are two main variations available today.
Trezor One
The original model, simple and reliable. It supports most cryptocurrencies and remains affordable for beginners.
Trezor Model T
The advanced version, featuring a touchscreen, faster processor, and broader crypto support.
| Type | Features | Best For |
|---|---|---|
| Trezor One | Basic, affordable, secure | Beginners & casual users |
| Trezor Model T | Touchscreen, advanced functions | Serious traders & investors |
How does Trezor Wallet work?
This wallet works by storing private keys offline and requiring physical confirmation for every transaction. When connected to your computer, it signs transactions internally without exposing private keys. This makes it nearly impossible for malware or remote attackers to steal your crypto.
Pros & Cons
Before investing in Trezor Wallet, it helps to weigh the benefits and drawbacks.
Pros
Keeps assets offline and secure
Trezor is a hardware wallet, meaning your private keys are stored offline, away from the internet. This drastically reduces the risk of hacks, phishing attempts, or malware stealing your crypto compared to hot wallets.
Easy to use with a simple interface
Despite being a physical device, Trezor is designed with user-friendliness in mind. Its interface and step-by-step setup make it accessible for both beginners and advanced users, so you don’t need deep technical knowledge to secure your assets.
Recovery seed ensures backup
During setup, Trezor generates a recovery seed phrase. This acts as a fail-safe, allowing you to restore access to your funds if the device is lost, damaged, or replaced—so long as the seed is kept safe and private.
Works with multiple cryptocurrencies
Trezor supports a wide range of coins and tokens, from Bitcoin and Ethereum to lesser-known altcoins. This makes it versatile for users who want to store and manage a diverse crypto portfolio in one secure device.
Cons
Cost compared to free software wallets
Unlike mobile apps or browser-based wallets that are free, Trezor is a paid product. While the cost is justified by its security, it may be a barrier for beginners or those investing only small amounts.
Requires physical device
Since it’s a hardware wallet, transactions require plugging in the device and physically confirming them. While this adds security, it may feel less convenient than using a software wallet on your phone.
Must be protected from loss or theft
If someone steals or finds your Trezor device and also gains access to your recovery seed, your funds are at risk. The wallet itself must be safeguarded like any other valuable.
Some learning curve for beginners
New users may initially find it intimidating to set up recovery seeds, confirm transactions on the device, and understand the importance of offline storage. However, with practice and guidance, it becomes straightforward.
| Pros | Cons |
|---|---|
| Keeps assets offline and secure | Cost compared to free software wallets |
| Easy to use with simple interface | Requires physical device |
| Recovery seed ensures backup | Must be protected from loss or theft |
| Works with multiple cryptocurrencies | Some learning curve for beginners |
Uses of Trezor Wallet
The wallet has several practical uses in the crypto ecosystem.
Long-Term Storage
It’s ideal for holding crypto safely over years. Investors can “HODL” without worrying about exchange hacks.
Active Trading Support
Even active traders use it to secure funds between trades. It integrates with exchanges and apps while still requiring confirmations.
Business Security
Companies dealing with crypto payments rely on this wallet to protect customer and transaction data.
Compliance and Privacy
In an era of increasing surveillance, tools like Trezor Wallet provide privacy. It works well alongside services like Express VPN, creating layered security for sensitive transactions.
A friend once asked me, “Is Trezor safe compared to leaving crypto on exchanges?” My answer was simple: “Yes. Exchanges can be hacked, but with Trezor Wallet, the keys are yours.” This independence is why many experts consider hardware wallets a must-have in protecting digital wealth. Without one, you risk exposure to constant cyber threats lurking online.
Conclusion
Trezor Wallet is more than a tool—it’s peace of mind in the unpredictable world of crypto. By keeping private keys offline and requiring physical confirmation, it ensures your assets stay under your control. In an era of rising cyber threats, understanding how it works and using it wisely helps you trade, invest, and hold with confidence.
Resources
- Trezor – Official Website
- Ledger vs. Trezor – Hardware Wallet Comparison – Cointelegraph
- CryptoSec – Why Hardware Wallets Matter
- Binance Academy – What Is a Hardware Wallet?
- Investopedia – Best Crypto Wallets of 2025
