In the vast world of cybersecurity, one of the most overlooked dangers doesn’t come from hackers on the outside—it comes from within. The term Insider Threat refers to risks that arise when trusted individuals misuse their access to harm an organization. That could mean a disgruntled employee leaking data, a careless worker clicking on a phishing email, or even a contractor stealing sensitive information. Understanding this threat is crucial in today’s digital era, where even one mistake can cause massive damage. As companies rely more on connected systems and digital operations, the potential for internal risk grows. Learning to identify and manage insider threats isn’t just a technical task—it’s about creating a culture of awareness, responsibility, and trust.
What is Insider Threat

An Insider Threat is any risk that comes from someone within an organization who has authorized access to its systems, networks, or data and uses that access—intentionally or unintentionally—to cause harm. These insiders could be employees, contractors, partners, or anyone else who can access company information. Other terms you might hear include “internal threat,” “employee risk,” or “trusted insider attack.”
Unlike external hackers, it knows the company’s systems, policies, and weaknesses intimately. That makes them harder to detect and more dangerous. In cybersecurity terms, it’s like having an intruder who already has the key to your front door.
Breaking Down Insider Threat
To understand more about the threat, imagine your organization as a secure fortress. You might have high walls, guards, and alarms to keep outsiders away—but what if someone inside the castle decides to open the gates? That’s exactly how an insider threat works.
There are typically two main forms: malicious insiders and negligent insiders.
- Malicious insiders deliberately steal, leak, or sabotage data for personal gain or revenge.
- Negligent insiders, on the other hand, don’t intend harm but cause it through careless mistakes—like sharing passwords or clicking unsafe links.
One famous example occurred when an employee at a major financial institution downloaded sensitive client data onto a personal drive, exposing millions of accounts. The employee didn’t think it was dangerous, but the oversight caused a massive breach.
Key components of Insider Threat include:
- Access Control: Managing who can access what information.
- User Behavior Monitoring: Tracking unusual actions like mass file downloads or off-hour logins.
- Training and Awareness: Teaching staff how to recognize suspicious activities.
- Incident Response Plans: Ensuring there’s a clear process when a threat is detected.
Organizations also use advanced tools powered by artificial intelligence to detect anomalies. But technology alone isn’t enough. True defense comes from combining smart tools with a culture of transparency and accountability.
When leaders share why security matters, employees feel part of the mission. They’re less likely to make careless mistakes and more likely to report red flags. Effective threat management is as much about human behavior as it is about firewalls and encryption.
History of Insider Threat
The concept of Insider Threat dates back to the early days of information security. Long before the internet, companies struggled with internal theft and espionage. As technology evolved, so did the ways insiders could cause harm—from stealing paper documents to manipulating digital systems.
| Year | Event | Impact |
|---|---|---|
| 1986 | The first recorded insider data theft | Highlighted risks from internal employees. |
| 2000s | Rise of corporate espionage | Companies began creating insider threat programs. |
| 2010s | Digital transformation era | Increased remote access led to new vulnerabilities. |
| 2020 | Pandemic & remote work boom | Expanded the scope of insider threats globally. |
| 2023 | AI and automation in detection | Improved early detection through behavioral analytics. |
Today, this kind of threats are recognized as one of the top cybersecurity challenges, prompting both public and private sectors to invest heavily in prevention programs.
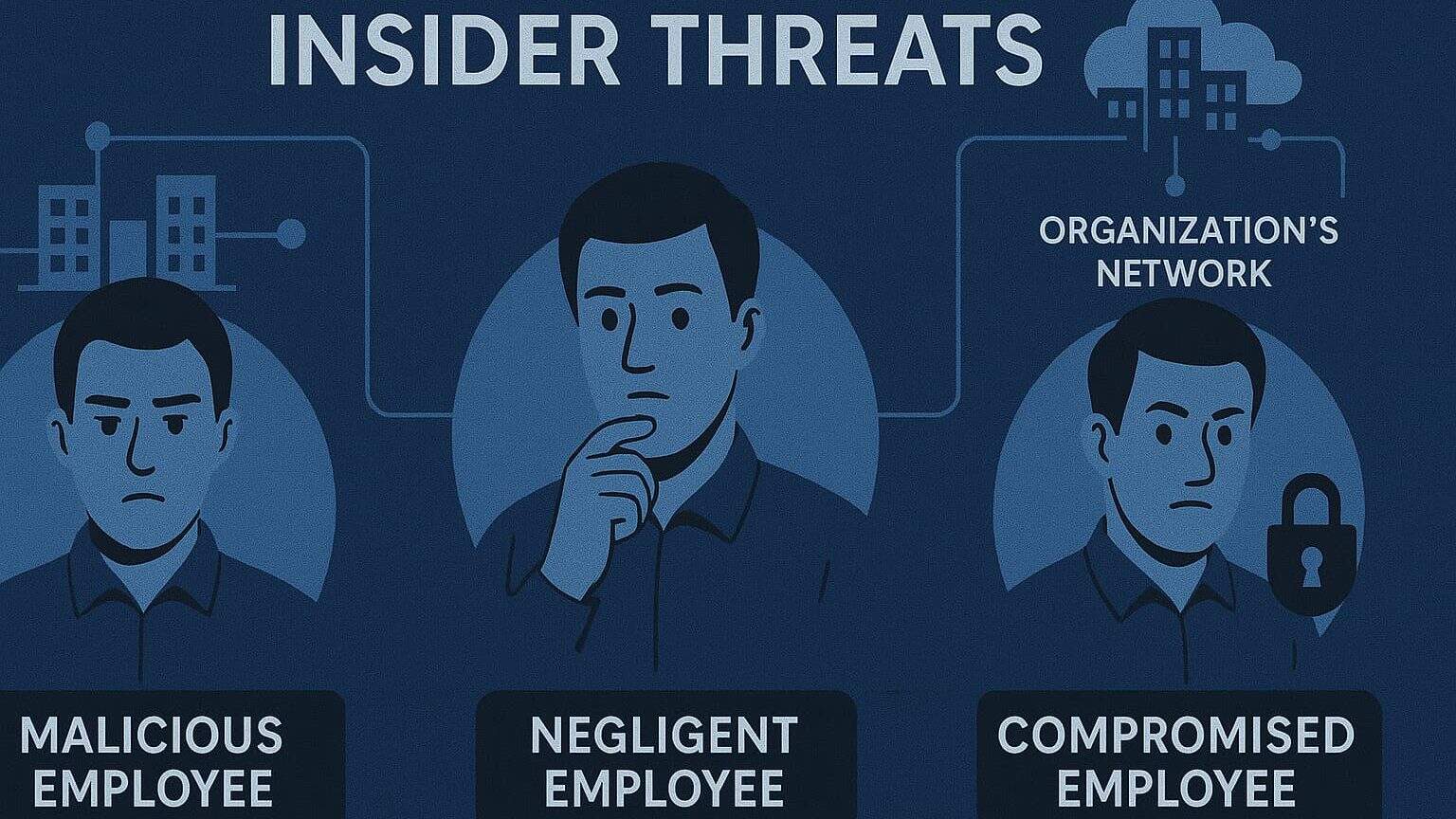
Types of Insider Threat
Malicious Insider
A person who intentionally misuses access for personal benefit or to harm the organization.
Negligent Insider
Someone who unintentionally creates vulnerabilities through careless actions.
Compromised Insider
An employee whose credentials are stolen and used by an outsider to infiltrate the system.
| Type | Description | Example |
|---|---|---|
| Malicious | Deliberate data theft or sabotage | Disgruntled worker leaks trade secrets |
| Negligent | Accidental security breach | Employee sends sensitive data to wrong address |
| Compromised | External control through stolen credentials | Hacker uses employee login to steal files |
How Does Insider Threat Work?
It starts when someone with authorized access performs an action that violates trust—whether intentional or not. It often begins subtly: downloading extra data, ignoring a security alert, or misusing login credentials. Cybersecurity teams use monitoring tools to detect unusual patterns, like large data transfers or repeated access attempts outside working hours.
When flagged early, these threats can be contained before major damage occurs. The process involves continuous observation, strong access controls, and employee education. Like trading strategies in finance, security teams must adapt constantly to changing tactics and trends.
Pros & Cons of Insider Threat
| Pros | Cons |
|---|---|
| Improves data protection and trust. | May raise privacy concerns among staff. |
| Detects internal risks before damage occurs. | Requires ongoing investment and training. |
| Builds a proactive security culture. | False positives can cause unnecessary alerts. |
| Enhances compliance with regulations. | Over-monitoring can reduce employee morale. |
Overall, insider threat programs strike a balance between security and privacy, ensuring organizations stay safe while maintaining employee confidence.
Uses of Insider Threat
The power of Insider Threat awareness lies in prevention. Organizations across industries use structured programs to detect suspicious behavior and stop breaches before they happen.
Business and Corporate Environments
Companies integrate insider threat monitoring into daily operations. These systems analyze employee behavior, report anomalies, and protect intellectual property. For example, in finance, this helps prevent internal fraud that could disrupt the Economic System.
Government and Defense
Government agencies manage insider threats to safeguard national secrets and public trust. With sensitive data constantly exchanged, one mistake could have serious consequences.
Healthcare and Education
Hospitals and universities handle personal and confidential data. A single insider leak can violate privacy laws and ruin reputations. Preventive training and real-time monitoring systems are crucial here.
Technology and Investment Firms
In tech companies like Microsoft and Google, insider threats can expose source codes or product plans. Investment firms use insider threat analysis to secure trading platforms, protect investment plan data, and prevent insider trading scandals that could trigger a market crash.
Just like choosing the Best stocks to buy, managing insider threats requires research, patience, and a smart approach. A well-trained workforce and robust detection tools act as the ultimate defense line against both human error and malicious intent.
Ultimately, Insider Threat awareness isn’t about suspicion—it’s about empowerment. When everyone in an organization understands their role in cybersecurity, the collective defense becomes stronger than any individual weakness.
Resources
- CISA: Insider Threat Mitigation Guide
- IBM Security: Understanding Insider Threats
- Checkpoint: The State of Cyber Security 2025
- Verizon: Data Breach Investigations Report
- exabeam: The Ultimate Guide to Insider Threats
