Zero Trust is a modern cybersecurity framework designed to remove the assumption of trust inside digital systems. Unlike legacy security models, which treated everything within the network perimeter as safe, Zero Trust requires strict identity verification, ongoing monitoring, and least-privilege controls for every action. The meaning of Zero Trust is captured in its philosophy: “never trust, always verify.”
By eliminating blind trust, this approach reduces risks associated with compromised accounts, insider threats, and lateral movement by attackers. The framework is now considered essential for businesses operating across cloud services, hybrid workforces, and global supply chains.
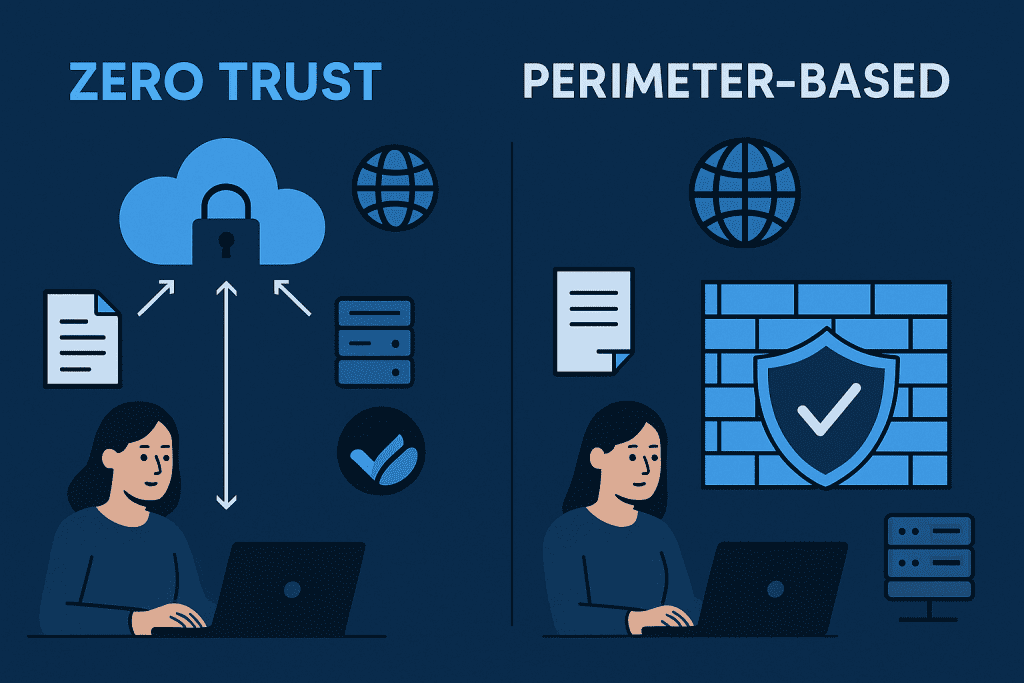
What is Zero Trust?
Zero Trust is a modern cybersecurity framework that eliminates the assumption of trust within digital systems. Instead of believing that everything inside a network is safe, it requires every user, device, and application to prove its legitimacy—every single time.
This approach is often described as “never trust, always verify.” It means that no matter if you’re an employee working in the office, a remote contractor, or a cloud application, access isn’t granted automatically. Synonyms for Zero Trust include Zero Trust Security Model and Zero Trust Architecture. All highlight the same principle: trust must always be earned, never assumed.
Breaking Down Zero Trust
The beauty of it lies in its simplicity, but implementing it can feel complex. Let’s break it down into its core components.
Continuous Verification
Access isn’t just checked once at login. Instead, users and devices are continuously monitored during their sessions. Imagine swiping your ID card not just when you walk into a building, but each time you enter a new room.
Least Privilege
This principle ensures users only have access to the resources they absolutely need. Think of it as giving a guest in your house access to the living room but not your private bedroom.
Microsegmentation
Instead of one big open network, it divides systems into smaller zones. If an intruder sneaks in, their movement is limited to one zone rather than having free rein.
Assume Breach
Perhaps the boldest idea—it assumes attackers are already inside. By designing defenses with this mindset, organizations can reduce damage and spot unusual activity faster.
For example, consider a hospital using it. Every doctor must verify their identity before accessing patient records, and even then, they only see the records relevant to their department. A hacker who somehow compromises one account cannot freely explore the entire system. This careful balance between access and restriction makes it a highly adaptive and practical approach for the modern digital world.
History
The concept of it began in the late 2000s when experts realized perimeter security—firewalls and “castle-and-moat” strategies—were failing. Phishing, stolen credentials, and insider threats were bypassing traditional defenses with ease.
| Year | Milestone |
|---|---|
| Late 2000s | The term “Zero Trust” was popularized as a new approach to cybersecurity. |
| 2010s | Cloud adoption highlighted the weaknesses of perimeter-only defenses. |
| 2020 | The U.S. federal government mandated Zero Trust strategies for modernization. |
| Today | Global standards from organizations like NIST guide adoption across industries. |
From Fortune 500 companies to small nonprofits, it is now a worldwide standard for securing systems against modern threats.
Types
While the principles remain the same, Zero Trust can be applied in different ways depending on the context.
Identity-Based
Focuses on verifying the user through multi-factor authentication (MFA) and biometrics.
Device-Based
Ensures that laptops, smartphones, and other devices meet security standards before gaining access.
Application-Based
Restricts access at the application level, requiring checks before using critical software.
Data-Centric
Applies policies directly to sensitive data, controlling who can view, edit, or move it.
| Type | Description |
|---|---|
| Identity-Based | Verifies user credentials and identity factors. |
| Device-Based | Checks the health and compliance of devices. |
| Application-Based | Secures critical apps with extra verification. |
| Data-Centric | Focuses protections on the data itself. |
How does Zero Trust work?
At its core, it works by applying dynamic verification policies to every request. For example, if you’re logging in from an unusual location, you might be asked for extra authentication. It looks at identity, device health, behavior analytics, and even geolocation before deciding if access should be granted. This constant, context-aware checking makes it nearly impossible for attackers to sneak around undetected.
Pros & Cons
Before rushing to adopt its, it’s worth looking at both sides.
| Pros | Cons |
|---|---|
| Strong defense against insider threats. By verifying every action, it minimizes the damage a malicious insider or compromised account can cause. | Setting it up requires investments in identity management systems, multi-factor authentication, and continuous monitoring tools, which may be expensive for smaller organizations. |
| Improved regulatory compliance. It aligns with compliance standards such as GDPR, HIPAA, and CCPA by ensuring strict identity verification, access logging, and data protection policies. | Frequent identity checks, MFA prompts, and access restrictions can frustrate employees if not implemented with user experience in mind. |
| Works seamlessly with cloud systems. It works across hybrid and multi-cloud environments, making it ideal for organizations using services like Azure, AWS, or Google Cloud. | Older applications and infrastructure may not support its policies natively, requiring costly upgrades or custom solutions. |
| Enhances customer trust. Adopting it demonstrates a proactive approach to data protection, which reassures customers and partners that sensitive information is safeguarded. | Transitioning from perimeter-based security to Zero Trust often requires step-by-step planning, strong governance, and cultural change, making adoption a long-term project. |
While the challenges are real, the benefits of adopting it almost always outweigh the drawbacks.
Uses of Zero Trust
So, how is it applied in the real world? Let’s look at some examples.
Microsoft. What is Zero Trust?
Explains the core principles of it and how Microsoft integrates the model across enterprise cloud environments to protect global businesses.
NIST. Zero Trust Architecture (SP 800-207)
Provides the official government standard that defines its principles and offers a framework for organizations to adopt it securely.
Microsoft. Zero Trust Strategy & Architecture
Outlines Microsoft’s approach to implementing it through identity, devices, apps, infrastructure, and data layers in real-world enterprise settings.
NIST. Implementing a Zero Trust Architecture (SP 1800-35)
Offers practical guidance and reference architectures to help IT teams transition from perimeter-based defenses to a model.
Microsoft. Zero Trust Deployment Plan with Microsoft 365
Provides a step-by-step deployment guide for organizations adopting Zero Trust using Microsoft 365, ensuring secure identity management and compliance.
Conclusion
Zero Trust is no longer just a cybersecurity buzzword—it is a critical framework for protecting organizations in a world where threats are constant and boundaries are blurred. By embracing principles like continuous verification, least privilege, microsegmentation, and the assumption of breach, businesses can reduce risks from insider threats, compromised credentials, and advanced attacks.
Resources
- NIST. Zero Trust Architecture
- Microsoft. Zero Trust Guide
- Google. BeyondCorp Zero Trust Model
- Okta. Zero Trust Security Solutions
- Forrester. Zero Trust Research
