I still remember the sinking feeling when my trusty laptop suddenly crawled to a halt every click felt like wading through molasses. That day I discovered the hidden menace of malicious software, and my search for a reliable defender led me to Malwarebytes. In the fast-paced world of computer security, where threats evolve daily, having a guardian that senses danger before it strikes is absolutely vital.
As part of the broader category of computer security software, Malware bytes have carved out a reputation for being both user-friendly and ruthlessly effective. Whether you’re a casual browser worried about shady downloads or an IT pro managing hundreds of endpoints, understanding what makes Malware bytes tick is the first step toward bulletproofing your digital life.
What is Malwarebytes?
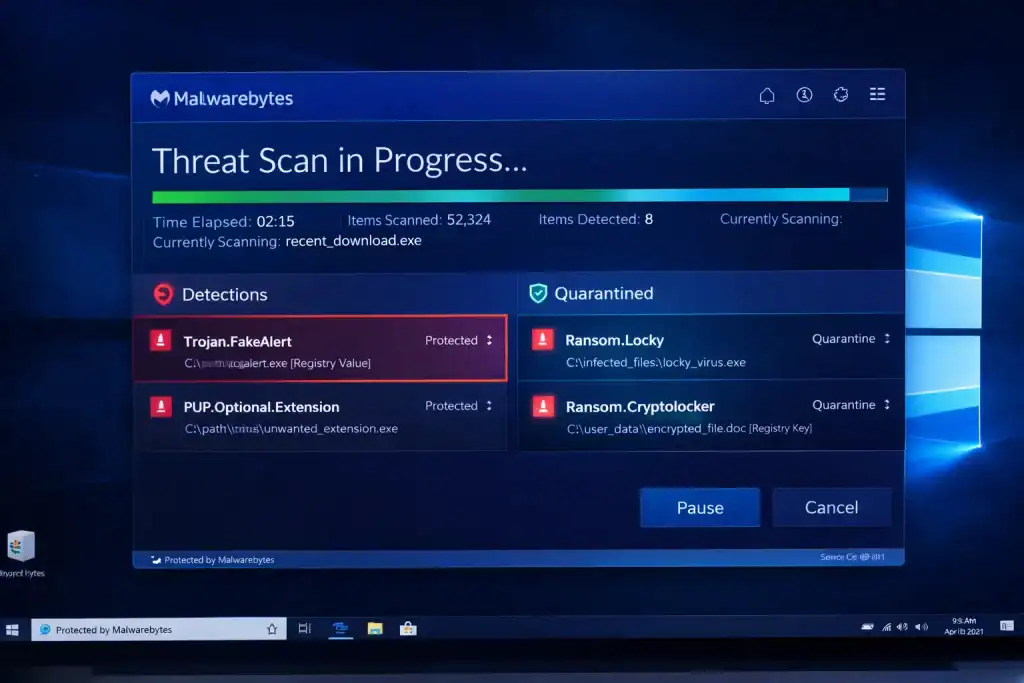
At its core, Malwarebytes is a truly next-generation anti-malware powerhouse, meticulously engineered to detect, neutralize, and remove even the stealthiest threats that traditional antivirus tools sometimes fail to catch. Rather than bloated security suites that slow your system to a crawl, Malwarebytes zeroes in on malicious code with surgical precision blending signature matching, heuristic behavior monitoring, and machine-learning insights to stay one step ahead of evolving attacks.
Its lightweight footprint ensures minimal performance impact, while real-time protection shields you from Trojans, ransomware, rootkits, adware, and zero-day exploits as they emerge. Deployed alongside your existing endpoint defense, Malwarebytes acts as both a rapid cleanup utility and a proactive watchdog, restoring system integrity and peace of mind for casual users and IT professionals alike.
Breaking Down Malwarebytes
To appreciate how Malware bytes stand out, let’s unpack its key components:
- Real-Time Protection Module: Continuously patrols your system for suspicious activity, quarantining threats before they execute.
- Threat Scan Engine: Runs deep scans of files, registry entries, and memory processes to root out hidden malware.
- Cleanup Utility: Offers one-click remediation for stubborn infections, even repairing damage caused by persistent threats.
Imagine you’ve downloaded what you thought was a harmless PDF, only to have it trigger a stealthy backdoor. Traditional antivirus might shrug and call it a “potentially unwanted program,” but Malware bytes hunts down the installer, shreds its payload, and patches any associated registry changes often in a matter of seconds.
History of Malwarebytes
Since its inception, Malware bytes have evolved from a simple anti-malware utility into a full-blown endpoint protection platform. Below is a snapshot of its journey:
| Year | Milestone |
|---|---|
| 2008 | Malware bytes founded by Marcin Kleczynski in Santa Clara, California |
| 2009 | Release of Malware bytes Anti-Malware (MBAM) free edition |
| 2012 | Introduction of the Premium subscription for real-time protection |
| 2015 | Expansion into business and enterprise markets with centralized console |
| 2018 | Launch of Malware bytes Nebula cloud management platform |
| 2021 | Integration of breach remediation and exploit mitigation technologies |
Types of Malwarebytes
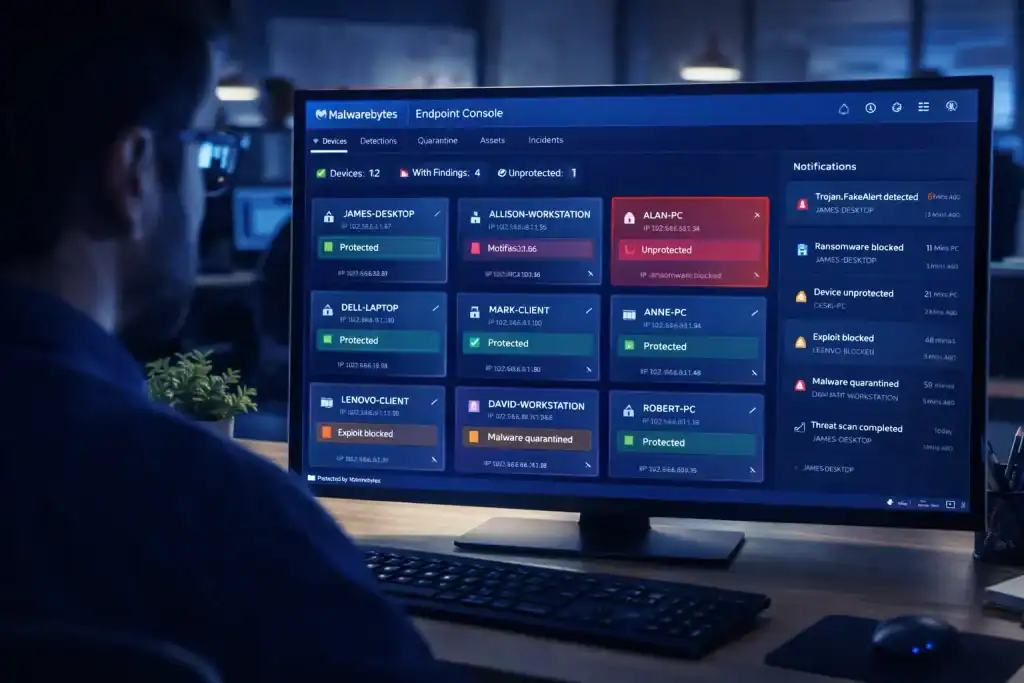
Offers tailored editions to suit different needs: Malwarebytes offers a variety of tailored editions each specifically designed to address the unique needs of home users, small businesses, and large enterprises alike, delivering everything from lightweight, on-demand scans to full-featured, cloud-managed endpoint protection.
Malwarebytes Free
A powerful on-demand scanner that excels at cleaning up infections after the fact. Great for occasional checks, it doesn’t offer real-time shields but packs a heavy punch when you initiate scans manually.
Malwarebytes Premium
For home users who crave continuous defense, Premium adds real-time monitoring, malicious website blocking, and automatic updates. It sits quietly in the background, stepping in the moment suspicious behavior is detected.
Malwarebytes Business (Endpoint Protection)
Designed for small to medium businesses, this edition extends real-time protection across multiple devices with an easy-to-use management console. Deploy in minutes and enforce company-wide security policies without a steep learning curve.
Malwarebytes Endpoint Detection and Response (EDR)
Built for larger enterprises, EDR augments real-time protection with threat hunting, incident response workflows, and deep forensic insights ideal for security teams that demand granular visibility and control.
How Does Malwarebytes Work?
Think of Malwarebytes as a tireless digital bloodhound and unblinking watchdog: once unleashed, it prowls through every nook and cranny of your system scanning files, dissecting running processes, probing memory for hidden code, and monitoring network connections for suspicious traffic to sniff out even the most cunningly concealed threats before they can strike. It doesn’t just rely on known signatures; it watches for strange behavior, odd file modifications, and unauthorized attempts to encrypt or exfiltrate your data, adapting on the fly to emerging dangers. Here’s a step-by-step overview:
- Initialization: On startup, the real-time protection module hooks into key system APIs to monitor for anomalies.
- Signature Matching: The threat scan engine compares file hashes and patterns against an extensive signature database, catching known malware instantly.
- Behavioral Analysis: Heuristic algorithms analyze process behavior if something tries to encrypt your documents without permission, it’s flagged on the spot.
- Quarantine: Confirmed threats are isolated in a secure vault, preventing any further damage.
- Remediation: The cleanup utility removes malicious files, reverses registry modifications, and repairs affected system components.
- Reporting & Updates: A concise report details what was found and cleaned, while background updates ensure your defenses adapt to the latest attack techniques.
Pros & Cons
Malwarebytes undoubtedly packs a powerful punch delivering rapid threat detection, real-time protection, and a lightweight footprint but it isn’t perfect: the free edition lacks continuous shields, some advanced cleanup tools require a paid subscription, and deeply embedded rootkits can occasionally slip through its defenses.
| Pros | Cons |
|---|---|
| Lightweight footprint with minimal performance hit | Free edition lacks real-time protection |
| Excels at catching zero-day and stealthy threats | Premium features require a subscription |
| Intuitive interface that even non-techies love | Advanced business/EDR tools can be overkill for casual use |
| Rapid signature and database updates | Some bundled cleanup tools (like adwcleaner) feel basic |
Uses of Malwarebytes
The versatility of Malwarebytes shines through across a wide spectrum of real-world scenarios, seamlessly adapting to protect everything from a single home PC to dozens of corporate endpoints whether you’re cleaning up after a suspicious download on your personal laptop, enforcing security policies across an entire small-business network, or conducting in-depth threat hunting in a large enterprise environment.
Personal PC Cleanup
After accidentally clicking a dubious link, you can launch a Threat Scan to remove cryptojackers or browser hijackers that slow down everyday browsing.
Small Business Endpoint Defense
Install the business console to enforce real-time protection across retail POS systems, safeguarding customer data from ransomware outbreaks.
IT Incident Response
When a workstation reports odd file behavior, deploy Malwarebytes EDR to quickly hunt down indicators of compromise, collect forensic artifacts, and remediate at scale.
School & Library Environments
Use scheduled scans on shared terminals to ensure students and patrons aren’t exposed to malicious downloads or adware that can compromise privacy.
Resources
- Computer Hope. Malwarebytes Anti-Malware Definition
- PCMag. Malwarebytes Free Review
- Security.org. Malwarebytes Antivirus Review
- PCMag. Malwarebytes Premium Security Review
- Malwarebytes. Official Malwarebytes Website
